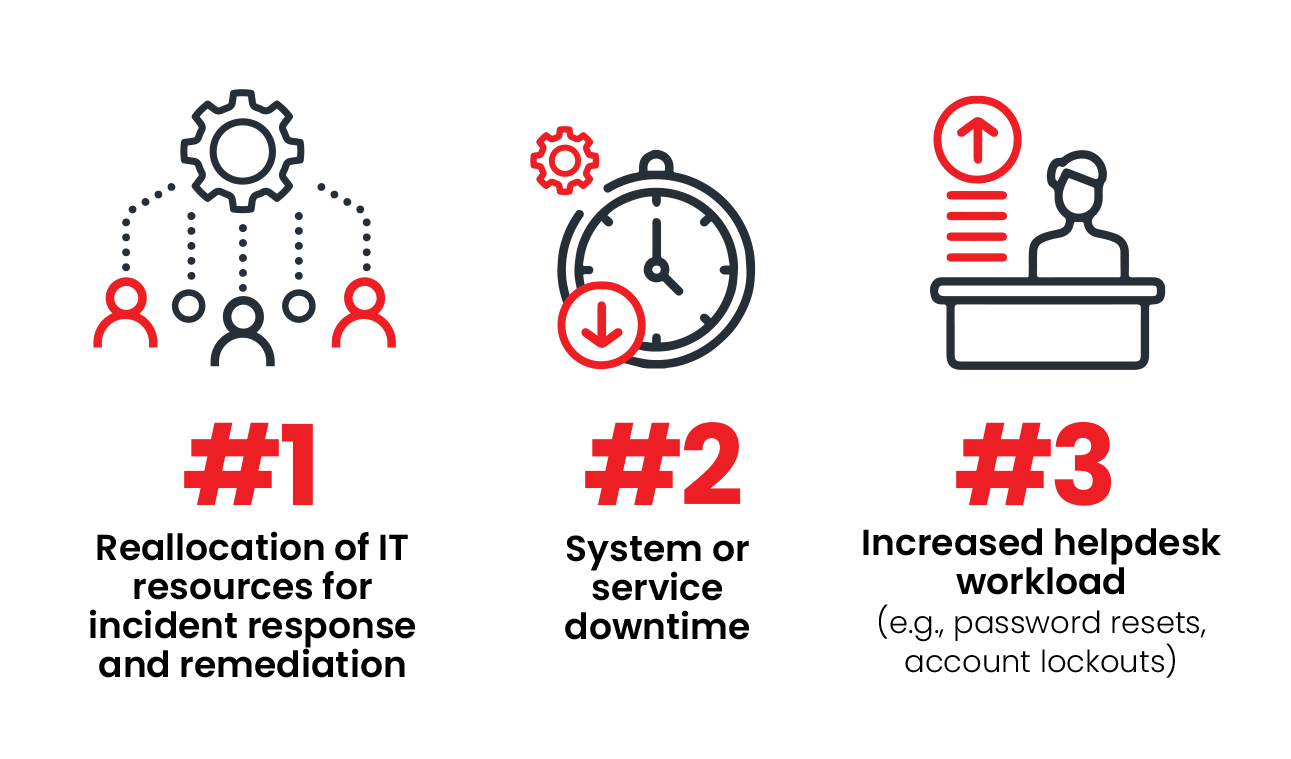
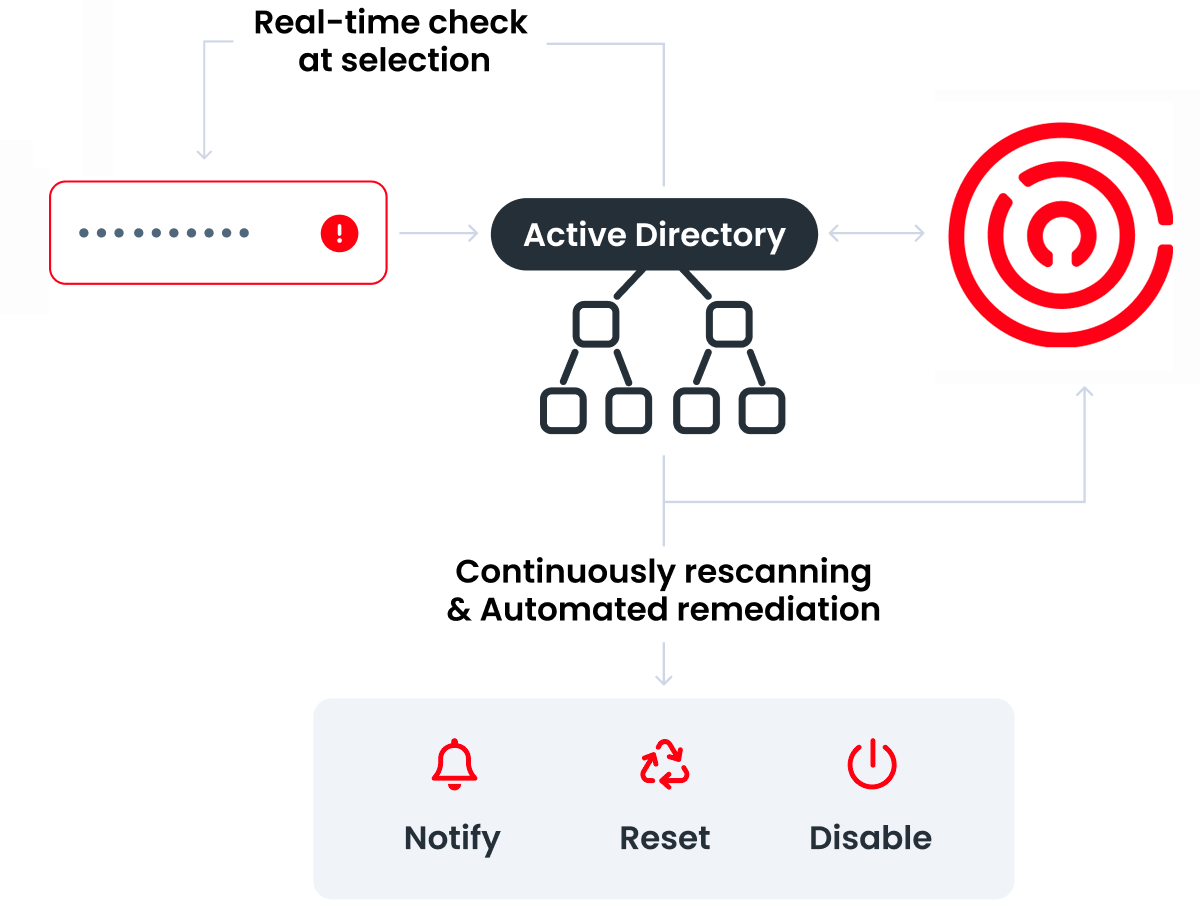
As organizations pivot toward more distributed and fragmented models of work, cybersecurity measures must adapt to keep pace with the evolving threat landscape and expanding attack surface.
In an in-depth interview with Chris Hines, VP of Strategy and Global Marketing at Axis Security, a recent acquisition by HPE, we explored the evolution of unified SASE as the next step in adaptive, integrated security solutions that address today’s complex challenges.
The Evolving Landscape of Remote and Hybrid Work
The COVID-19 pandemic, coupled with technological progress, has reshaped modern work environments. As organizations grapple with the change toward fragmented and dynamic work environments, the threat landscape and attack surface have expanded alongside, emphasizing the need for nimble and adaptive cybersecurity solutions that can address risks that originate both internally and externally: from malicious admins, end users, devices and threat actors aiming to exploit any weakness.
In this rapidly evolving landscape, traditional security architectures are no longer sufficient. Secure Access Service Edge (SASE) has emerged as a strategic imperative for businesses aiming to cope with new challenges and thrive in this new world. Notably, unified SASE offers an effective, streamlined approach to achieving robust security and efficient networking. This article explores the core aspects of unified SASE, why it’s essential for modern cybersecurity and how to get started on the SASE journey.
From Siloed Solutions to Unified Platforms
Historically, cybersecurity technologies such as Cloud Access Security Broker (CASB), Secure Web Gateway (SWG), and Zero Trust Network Access (ZTNA) were implemented to address distinct challenges. But as both IT environments and cybersecurity threats grow in complexity, there’s a clear shift towards integrated solutions.
Chris Hines underscores this transition, highlighting the complexity, cost and security challenges businesses face when managing multiple solutions, especially in a remote and hybrid work era. Moreover, vulnerabilities and user experience issues associated with traditional remote access technologies such as VPNs further exacerbate these challenges.
“There are three key factors driving the need for SASE adoption today: ineffective legacy security, unnecessarily complex networks, and obsolete solutions,” notes Chris Hines.
Enter Unified SASE
Introduced by Gartner in 2019, Secure Access Service Edge (SASE) emerged as a groundbreaking concept. It blends networking and security functionalities into a holistic policy-based platform, facilitating seamless collaboration between networking and security teams. Gartner predicts that “by 2025, 50% of new SD-WAN purchases will be part of a single-vendor SASE offering, up from 10% in 2022.”
Unified SASE converges the functions of network and security into a single, cloud-native platform, significantly reducing the complexities and inefficiencies associated with disjointed point solutions. It is based on two core technology sets:
- WAN Edge Services (SD-WAN): Software-Defined Wide Area Networking offers robust, flexible network connectivity. It automates the routing of network traffic to improve application performance and deliver a better user experience.
- Security Service Edge: Includes Zero Trust Network Access (ZTNA), Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Digital Experience Monitoring (DEM). This provides a comprehensive security layer by governing user access, filtering web content, managing cloud application use, and monitoring end-user experience.
Benefits of Unified SASE
By integrating WAN Edge Services and Security Service Edge into a single-vendor solution, unified SASE offers numerous advantages:
- Enhanced Security Posture: Universal security policies paired with centralized access controls heighten threat detection and response capabilities.
- Operational Efficiency: Merging networking and security functionalities minimizes complexities, promoting cross-functional collaboration.
- Improved User and Admin Experience: With automatic routing of traffic and enforcement of Zero Trust policies, both user and administrator experiences are optimized without compromise to security.
- Cost-Efficiency: A unified model inherently reduces capital and operational expenses, scaling seamlessly with evolving business requirements.
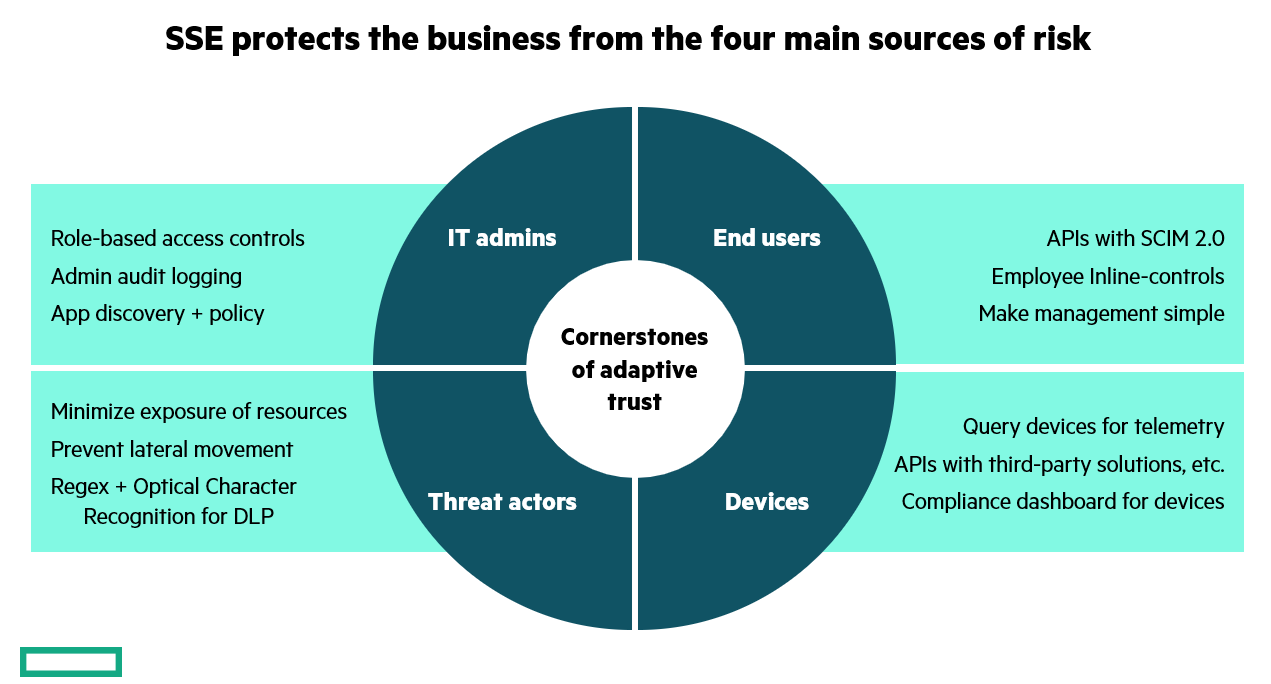
How to Begin Your Unified SASE Journey
Though implementing a unified SASE framework may seem daunting, with the right strategy and a reliable partner, you can make the transition to SASE smoothly and securely without disrupting existing operations.
Here are five key steps Chris Hines outlines that successful SASE implementations follow:
Step 1: Establish SASE Goals and Requirements
Determine your organization’s specific goals, needs, and criteria for a SASE framework. Evaluate your existing network and security infrastructure to identify any gaps, challenges, and available resources.
Step 2: Choose a Single-Vendor SASE Solution
Compare and assess different SASE vendors based on factors such as capabilities, coverage, performance metrics, scalability, reliability, customer support, and cost structure. Choose a well-architected, single-vendor SASE solution that is integrated, unified and easy to use.
Step 3: Formulate Your SASE Implementation Strategy
Collaborate with your chosen SASE provider to outline your network topology, security policies, user groups, app profiles, and connectivity options based on best practices. This step should be a joint effort with your SASE provider to ensure success.
Step 4: Initiate SASE Deployment in Phases
Start SASE implementation by deploying essential elements like agents, connectors, SD-WAN devices, or private PoPs via a central management dashboard. Migrate users, devices, physical locations, and applications to your new SASE architecture in a phased or batched manner. SASE’s flexibility allows it to work alongside existing solutions, offering you the pace of deployment that suits your team’s readiness.
Step 5: Unlock the Full Potential of SASE
As the deployment progresses, utilize the tools and dashboards provided by your SASE provider to gain operational insights and real-time visibility. This will allow you to fine-tune your SASE implementation and even discover new areas where SASE could add more value to your business.
By following these steps, you’ll be well on your way to leveraging the full potential of unified SASE, thereby strengthening your security posture and improving network performance.
Conclusion – Two Paths to Unified SASE
If you’re in the market for a powerful, single-vendor SASE solution that delivers both enhanced security and reliable connectivity from any location, you should consider the newly expanded offerings from HPE Aruba Networking, enhanced by its recent acquisition of Axis Security.
Already a leader in SD-WAN, the addition of Security Service Edge (SSE) to HPE Aruba Networking capabilities now provides the foundation for an even more comprehensive, unified approach to SASE suitable for today’s dispersed and dynamic business environments.
The acquisition of Axis Security amplifies HPE’s commitment to integrated network and security solutions. Axis Security’s expertise in Zero Trust Network Access (ZTNA) further enriches HPE Aruba Networking’s SASE capabilities through Adaptive Trust, adding advanced, granular access controls, superior threat detection, and real-time adaptive responses.
IT teams can now implement WAN and cloud security measures directly at the network edge through HPE Aruba Networking EdgeConnect SD-WAN, while also benefiting from Axis Security’s advanced ZTNA functionalities. This ensures that robust Zero Trust security controls can be extended to all users and devices, regardless of location.
Choosing a unified SASE solution from a single vendor can accelerate this digital transformation. The only remaining question is: How will you begin your SASE journey?
Two Entry Points for Your SASE Strategy
- Initiating with SSE and ZTNA: The recent Axis Security acquisition fortifies HPE Aruba Networking’s already robust security If ZTNA is your starting point, consider replacing your VPN with ZTNA from HPE Aruba Networking to enable additional layers of security for your private applications, whether they reside in a data center, the cloud, or in between.
- Starting with SD-WAN: If you prefer to begin your SASE journey by focusing on SD-WAN and completing your secure edge portfolio, then the full array of options powered by HPE Aruba Networking EdgeConnect SD-WAN is available.
According to a 2023 Ponemon Institute report, about 46% of organizations are expected to have a SASE architecture in place within a year. SASE is not just a fleeting tech trend; it’s a strategic imperative for any enterprise looking to thrive in the digital age. Adopting a unified SASE framework not only improves your organization’s security posture but also enhances operational efficiency and cost-effectiveness for the future.
For more information and to take a test drive of HPE Aruba Networking unified SASE, visit https://www.arubanetworks.com/connect-and-protect/.
The post Unlocking the Full Potential of Unified SASE: An Interview with HPE’s Chris Hines appeared first on Cybersecurity Insiders.
December 01, 2023 at 02:55AM