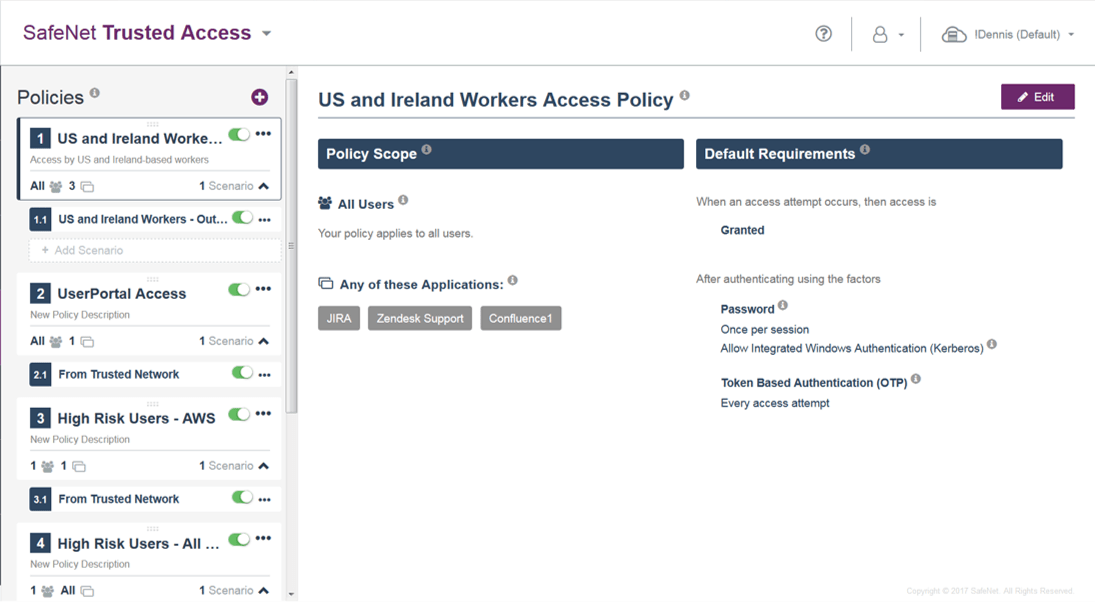
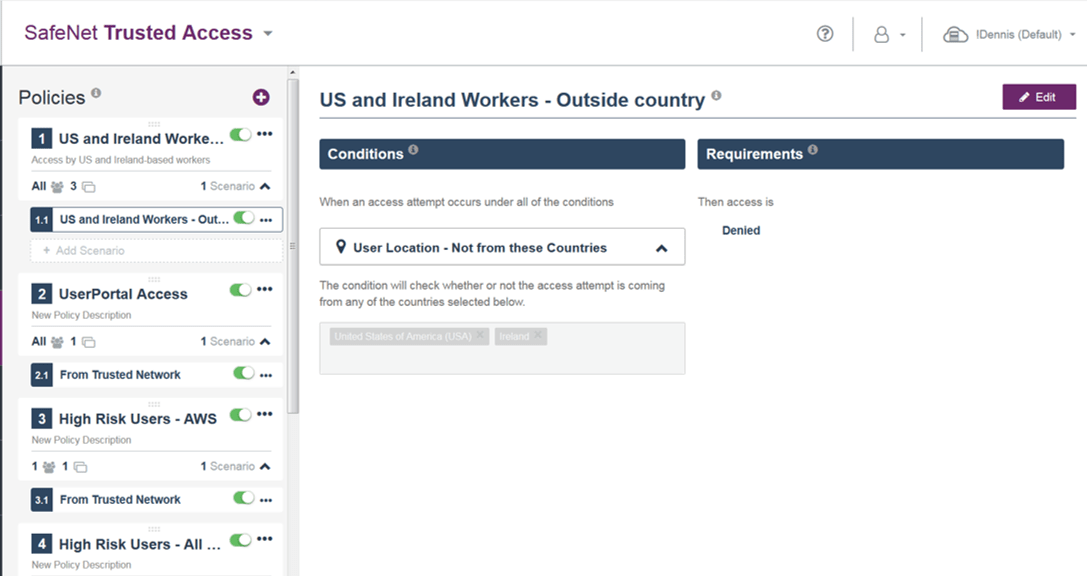
In the first two parts (Part 1 and Part 2) of this three-part series on the upcoming Personal Data Protection Bill in India, we covered the draft bill’s important elements and key terminologies that organisations need to keep in mind in order to comply with the bill’s stringent guidelines.
To quickly summarise what we have covered earlier, the Personal Data Protection Bill is slated to mark the advent of perhaps the biggest shake-up of data privacy laws in India. Based on the premise that ‘Right to Privacy’ is a fundamental right of every Indian citizen, the bill clearly outlines (in no ambiguous terms) the way in which organisations can obtain, store, process or access an individual’s personal data, and makes “individual consent” a central requirement for obtaining, storing, processing or accessing such personal data.
In this third (and last part) of the Personal Data Protection Bill series, we will cover 4 key technologies that play a pivotal role in protecting data — both at rest and in motion, and 3 important steps that organisations need to take to adhere to the bill’s mandates. Let’s begin!
Key Technologies
1. Data Encryption
Widely considered as one of the best ways of protecting any data, data encryption is the process of scrambling plain data into an unreadable format through the use of an algorithm that creates a unique “key” known as an “encryption key” or “crypto key”.
Encrypted data can be unscrambled back and made readable only with the specific key that was used to encrypt it. With massive advancements in encryption technologies in the last few years, encrypted data is virtually impossible to hack today.
2. Tokenization
Tokenization is the process of assigning a random surrogate value (also known as a “Token”) to the original data to avoid its easy identification.
Initiated using a special software known as a “Tokenization Manager”, the original data is first received at its initial entry point by the Tokenization Manager and then encrypted. As an industry best practice, many organisations across the globe then proceed to securely store the encryption keys in FIPS-certified Hardware Security Modules (HSMs).
A good Tokenization solution should be able to support reverse data tokenization (also known as “De-tokenization”) wherein the tokens can be converted back to plain data, as well as non-reversible data tokenization wherein the tokens cannot be converted back to plain data. Further, the solution should also offer key functionalities like bulk tokenization for operations that involve large data volumes and ready integration with a Key Management Solution (KMS) or HSM if crypto keys are involved in the tokenization operation.
3. Data Masking
Also known as “Data Obfuscation”, data masking is the process of hiding (or obscuring) the original data with random characters or other data. In data masking, a structurally similar but inauthentic version of the original data is created by using the same format as that of the original data, but changing the original values to achieve obfuscation.
The original data can be modified in a number of ways – including encryption, character shuffling, and character or word substitution. While any method can be used to mask the original data, the moot point is that the values must be changed in some way or the other to make detection or reverse engineering impossible.
The primary purpose of data masking is to protect the original data while having a functional substitute for occasions when the original data is not required. For example, Data Testing.
In India, the Payment Card Industry Data Security Standard (PCI DSS) and Reserve Bank of India (RBI)’s circular on tokenization of debit card data mandates the use of data masking to protect the card data.
4. Key Management
Since encryption keys pass through multiple phases during their lifetime – like generation, distribution, rotation, archival, storage, backup and destruction, efficiently managing these keys at each and every stage of their lifecycle plays a pivotal role in optimal data protection.
With an increasing range of heterogeneous keys being created by a diverse set of applications, efficiently managing these keys centrally becomes paramount. A common practice for cohesive key management is using the Key Management Interoperability Protocol (KMIP) – an extensible communication protocol that defines the message formats for the manipulation of crypto keys on a key management server.
KMIP seamlessly facilitates data encryption by simplifying crypto key management and is inherently designed to support a diverse set of cryptographic objects, including symmetric and asymmetric keys, digital certificates, etc. Further, it allows clients to ask a server to encrypt or decrypt data, without needing direct access to the encryption key.
With more and more organisations using a disparate set of crypto technologies (like Payment HSMs for financial operations, General Purpose HSMs for common operations, etc.) across multiple business units and diverse geographical locations, adopting a robust Key Management Platform that would cater to the current as well as future encryption requirements is imperative.
Steps for preparing for the Personal Data Protection Bill
Placing great emphasis on the approach of “privacy-by-design”, complying with the bill’s strict mandates requires all departments in an organisation to closely look at the way they manage their users’ data.
Below are 3 easy steps to audit your users’ personal data:
Step 1: Map Your Data
Carefully identify all the sources from where your organisation receives its users’ personal data, where it resides, which departments and individuals have access to it, and document in detail if there are any security risks to that data.
Step 2: Determine What Data You Want To Store, And Why
More often than not, organisations keep collecting data without any concrete plan of destroying it when it becomes redundant. Since the Personal Data Protection Bill encourages organisations to adopt a disciplined approach towards its users’ personal data, now is the right time to audit your data and determine which of it is important and which of it can be deleted.
Below are 3 pertinent questions that need to be asked:
1. Why are we storing all this data? Is all of it really business critical?
2. What is our business objective of collecting all categories of our users’ personal information? Do we really need all this information?
3. Is the financial gain of deleting this information greater than the cost of encrypting it?
Step 3: Review Your Cybersecurity Measures
Meticulously review your organisation’s existing cybersecurity systems and update/upgrade them wherever needed. While front-line (perimeter) defense mechanisms like firewalls, antivirus, antimalware, etc. act as a good deterrence against cyber attacks, they are rendered useless once hackers gain an inside access to an organisation’s data files.
To truly insulate your organisation from malicious attacks, equal priority needs to be given to last-line defense mechanisms like encryption, tokenization, data masking and key management.
Further, do not restrict the purview of cybersecurity to your organisation only, but extend it to your vendors too as mere outsourcing doesn’t exempt you from any breach of your users’ personal data.
To Sum It Up
With the Personal Data Protection Bill recommending hefty penalties that can go up to Rs. 15 crores or 4% of an organisation’s total worldwide turnover, organisations can no longer take their users’ personal data for granted.
Considering the recent example of France imposing a fine of €50 million (approximately Rs. 400 crores) on Google for violating data privacy rules as defined by the GDPR, it would be a folly on the part of Indian organisations to not take the Personal Data Protection Bill’s compliance guidelines seriously.
To comply with the bill’s stringent mandates, organisations need to adopt a data-centric approach towards cybersecurity to protect their users’ personal data.
Below are 3 basic steps that organisations can take to safeguard their users’ personal data:
Step 1: Encrypt The Data – at rest, in motion, on cloud and across virtual and on-premise environments.
Step 2: Own & Secure The Encryption Keys – at each stage of their lifecycle.
Step 3: Control Access – to resources across diverse environments by providing strong multi-factor authentication to prevent unauthorised access.
How Gemalto Can Help
As the global leader in providing state-of-the-art data protection technologies to leading organisations across the globe, Gemalto offers a robust, edge to core, plug-and-play Unified Data Protection Compliance Platform that organisations can leverage across diverse business needs.
Below is a quick snapshot of Gemalto’s Enterprise Data Protection Portfolio:

Learn how Gemalto can assist your organisation in optimal data protection.
The post Demystifying the India Data Protection Bill, 2018: Part 3 of 3 appeared first on Cybersecurity Insiders.
February 26, 2019 at 09:09AM