An Interview with Joe Green, Netskope
The number of employees working from home or other remote locations has skyrocketed since the outbreak of the coronavirus pandemic. This massive shift has led to a rise in the use of cloud applications and services, along with an increase in risky behaviors and a further blurring of the lines between personal and corporate IT resources.
We asked Joe Green, Global Director, Solution Architects, Netskope, about how to continuously manage these risks using the right cloud security and networking solutions.
In part 1 of our interview, Joe discussed the basic reliability of cloud security, and risks created by the increased number of people working from home, including device-related and malware risks, and strategies for managing these risks.
In part 2, Joe discusses the risk of data loss, the role of SD-WAN in contemporary networking and investment strategies for ensuring security in a direct-to-Net/direct-to-cloud world.
Enea:
We talked about malware in part 1 of the interview, so now let’s talk about data loss prevention. The Cloud/SaaS security survey, indicated a high level of concern about cloud file sharing and hosting and cloud email, all of which are important vectors for data loss as well as malware infection.

SaaS apps that generate the highest concerns for security
Do these concerns line up with what you’re hearing from customers? What strategies would you recommend to prevent data loss in the specific context of file sharing and email?
JG
This definitely aligns with what we’re seeing, so it’s not a surprise. File hosting or transfers and cloud email are two of the biggest applications people are using. Email is what everyone uses to communicate, and people are constantly sharing data. But it’s important to understand that there’s a difference between a malicious insider and an accidentally malicious insider. And companies, when they’re trying to protect their intellectual property (which all companies do), must worry about both. They have malicious people on the outside, they have them on the inside, and they have accidentally malicious people as well.

Communication and collaboration tools (such as Skype, MS Teams, Slack, etc.) are other SaaS apps that organizations are concerned about. Slack, for example, has become an incredibly popular tool and Microsoft Teams is growing at an unbelievable rate. I think there’s a need for education around these tools. In my observations, people are scrambling to learn how to support MS Teams, to learn how it works, how to secure it and we, at Netskope, are spending a lot of time supporting this education.
But, we can also look at this in terms of why it is a top concern. When you’re trying to protect intellectual property or trade secrets or anything else that flows out of a network, you have to have technology that understands the traffic, that knows the patterns you’re looking for. It’s about reducing false positives, because you can’t have people sifting through millions upon millions of records.
You need technology that is very accurate and can identify whether, for example, it’s a corporate template, national ID numbers, passport numbers, national registration numbers, or whatever, based on the country you live in. You want to make sure that your system can accurately recognize the data, detect the patterns you’re looking for, and keep the false positives very low, otherwise you just make the job impossible for security analysts.
Enea:
That’s interesting. So, if I understand correctly, to be effective, we need technology that can deal with data loss prevention (DLP) at the scale of the cloud.
J.G.
Absolutely, and it has to be able to function at that scale even when performing, real-time, in-line scanning. There’s an important difference between real-time security that is carried out in-line and scanning that happens out-of-band.
When you look at files in Google Drive or OneDrive or SharePoint, you may have data that’s already in the cloud. We call that data at rest. We scan it using something called application programming interface (API) scanning. This is a reactive, non-real-time technology because the data that is scanned is already in the cloud. It’s still very important to scan it, whether for malware or DLP patterns, but API scanning is a very reactive technology.

More important is the in-line, real-time technology. It doesn’t matter whether the data is going through a client, an explicit proxy in the cloud, or whether it’s an upload or a download, the important thing is that it’s in-line and real-time, that’s where we need to focus. And because the cloud can be worldwide, it’s also important to develop security that follows users no matter where they go.
Enea:
It’s interesting you should say that because findings from the Cloud/SaaS security survey support this approach:
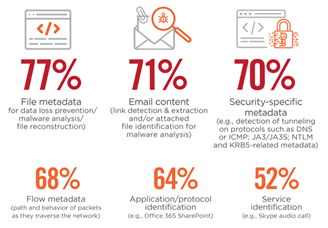
Types of traffic analysis cloud/SaaS providers should be using to properly understand and secure customer activities
J.G.
The global pandemic has exacerbated this aspect of security because when users went home to work, that could mean a flat in London, an apartment in Hong Kong or a house in America. And in reality, it doesn’t matter where it is. Any user can go to any coffee shop to work now, but wherever they might be, their organization still needs to secure their data.
In legacy solutions, the security stacks were built on-prem at a company. But nowadays it doesn’t make any sense to route a user through VPN technology, back to a corporate, on-prem branch office and then do a U-turn to go back out to the Internet to a cloud application. Everything should be direct-to-net or direct-to-cloud. Security should be real-time and in-line, no matter where the user is. If a company is using Netskope technology for example, users come through the Netskope cloud and straight to their application. Our security technology is completely invisible to the user. They are accessing the application natively, like they normally would, but the security is happening in real-time, in-line, and they don’t even know about it.
Enea:
Indeed, if you think of the user and data as being at the heart of the enterprise (rather than in terms of networks, servers, cables, etc.), it changes the way you approach security. Which brings us to SD-WAN.
SD-WAN has become very popular. It can be deployed on premise or in the cloud, and enables the dynamic provisioning of virtualized network services, like firewalls, session controllers or load balancers, according to specific security and performance requirements. And it takes away the need to backhaul traffic through a hub or a headquarter data center.
Have you seen an increase in SD-WAN out in the field? How does a cloud-native security platform like Netskope’s correlate with SD-WAN?
J.G.
Yes, there has been a huge increase in SD-WAN, but it’s not a technology that Netskope makes or sells.
The reason SD-WAN has been adopted so much is because companies are trying to move away from expensive, private MPLS links that connect their offices worldwide. These links require very special and expensive proprietary hardware, such as routers. SD-WAN represents almost immediate cost savings that not only helps with wide area networks, but also helps to improve performance and traffic prioritization, among other things.

Now the irony is that when everyone went home at the beginning of the pandemic, SD-WAN deployment continued to accelerate. In reality, it should have become a low priority for companies. But, the interesting thing I discovered when talking to customers, is that since their employees are now remote, they’re actually using this time to upgrade their infrastructure and get rid of the expensive private lines and move to public links, which SD-WAN can take advantage of.
What’s interesting for Netskope is that there’s no competitive overlap. We can establish direct tunnels between any SD-WAN technology and Netskope. When the traffic hits, anything destined for the web or for a cloud application goes through the SD-WAN. A policy-based routing decision is then made whereby any traffic destined for a cloud application is sent to Netskope. This is completely transparent to the user, they have no idea it’s going on. It goes right back to what I was saying earlier, it’s a direct-to-net or direct-to-cloud feature, where you’re not backhauling traffic, you’re not sending traffic to a location that it doesn’t really need to go to
So, to answer your question, Netskope integrates tightly with SD-WAN vendors and works with them. Traffic is directed right from the SD-WAN box to the Netskope security cloud, which is worldwide, and we do all the decryption and traffic inspection processing. This is a seamless solution going on in the background. The customer or end-user has no idea it’s there, but at the end of the day it’s delivering a much better experience for the user.
Enea:
The SASE concept certainly does seem well-suited to the fundamental changes underway in the way we work. Interestingly enough, security professionals who participated in the Cloud/SaaS security survey also indicated they planned to invest in additional on-premise component solutions like endpoint security, UTM & NG firewall, and IDS/IPS.

New or additional deployments of solutions planned in response to increased external threats from cloud/SaaS usage
What do you think about such plans?
J.G.
Because of the vendor I work for, my opinion could be seen as slightly biased! However, I also talk to hundreds of customers worldwide, and I can therefore tell you with absolute certainty that the investment in on-prem solutions goes down by the day. And the global pandemic exacerbated that trend. Late starters, slow runners, even the most conservative financial companies, everyone was forced to accelerate the move to the cloud following the onset of the pandemic. They are all pivoting as fast as humanly possible to get to the cloud, maybe not for everything, but for most of their users. So, I definitely see the spend in on-prem going down as we help people get off their legacy on-prem proxy servers and DLP solutions.
Enea:
So, for you, we are no longer in the next-generation, but in the next, next-generation?

J.G.
Exactly, we’ve been calling the next-generation firewall the next generation for twenty years. If you have a firewall which is on prem, even the best – and all the main vendors are battling it out to build the top next-generation firewall – but none of your users are actually sitting behind that firewall, is that really next generation technology? Or did that become a legacy technology overnight? And that’s where my conversations have pivoted to “let’s talk about your perimeter.” “What is the perimeter of your network today?” And this question alone causes customers to think in a completely different way from the way they’ve been thinking for probably the last fifteen to twenty years. So, we have definitely seen a pivot. On-prem is dropping at the speed of light and the adoption and spend on cloud technology is dwarfing it day-by-day.
Enea:
Breaking with the way they’ve thought about security for the last couple of decades is probably difficult for some security professionals. What parting advice do you have for them as the cloud/WFH world becomes our new normal.

J.G.
Take a deep breath and remember you don’t have to stress over whether or not to migrate to the cloud. It’s already happened. Your people, your data and your apps are there. So go with the flow and don’t try to hitch a team of horses to an automobile. To make sure you’re not tempted, keep in mind the simple rule: “don’t send traffic to a location that it doesn’t really need to go to,” either for connectivity or security handling. With the right partners, you can deliver networking and security as integrated cloud services to protect your users and data wherever they are, and your infrastructure will line up naturally with the way people are actually working today.
Enea:
Joe, thank you so much for these insights. If I can sum up, I would say that your message is to embrace the change and shift cloud networking and security to the top of your investment priorities. And to find an experienced partner who can accompany you.
The post Cybersecurity for a Cloud-First, Work-from-Home World (Part 2) appeared first on Cybersecurity Insiders.
February 20, 2021 at 12:33AM


















