An Interview with Joe Green, Netskope
Key takeaways
- There are risks associated with a remote workforce and the at-home use of business devices and IoT devices, but the right tools are available now to continuously manage these risks.
- There is an ongoing increase in cloud-delivered malware, and more data loss via cloud file sharing, hosting, and email. However, the technology already exists to protect against these threats.
- Agility is critical in both networking and security in the mobile/remote/work-from-home (WFH) world. SD-WAN can help deliver this networking agility, and it can integrate seamlessly with cloud-delivered security services, fulfilling the promise of the SASE paradigm.
- Don’t keep investing in legacy on-premises solutions when your users, data and applications have moved out of the office and onto the cloud. Embrace the change and shift cloud networking and security to the top of your investment priorities.
The number of employees working from remote locations has skyrocketed since the outbreak of the coronavirus pandemic. This massive shift has accelerated the use of cloud applications and services, along with an increase in risky behaviors and a further blurring of the lines between personal and corporate IT resources.
We asked Joe Green, Global Director, Solution Architects, Netskope, about how to continuously manage these risks using the right cloud security and networking solutions.

Joe Green, Global Director, Solution Architects, Netskope
Part 1
In part 1 of our interview, Joe discusses the risks created by the increased number of people working from home and how organizations can manage these risks.
Enea:
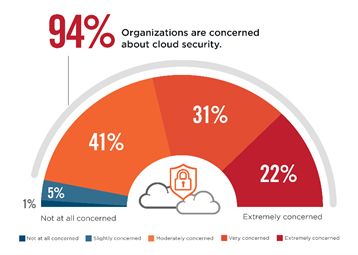
In a recent survey on CISO concerns and plans for Cloud/SaaS security, carried out by Cybersecurity Insiders, 94% of respondents said that their organization was concerned about cloud security with 22% extremely concerned. Are cloud services riskier than on-premise IT systems? How worried should organizations be about moving to the cloud?
Joe Green:
Well first, it should be understood that the majority of network activity is not on premise anymore, it’s already moved to the cloud. Right now, we are seeing over 85% of all network traffic going directly to the cloud. Whether people are themselves on premise, or at home or in a coffee shop, they’re accessing applications and data in the cloud. And, in any case, you can’t just make an assumption that because something is on premise it is more secure, or because it’s in the cloud it’s less secure.
It’s not really about how secure the cloud is, or applications or on-premise resources. It’s about focus and perspective on the right solutions. If you look at it through the lens of a cloud security company, or a cloud provider, that’s their business. But when you’re a company running a business, manufacturing a product or selling a service, that’s going to be your main focus, not the cloud and not security. So, when I’m talking with customers, it’s important for me to tell them that security is my business, and where I’m involved, the cloud will probably be more secure. And with cloud-delivered security, you, as a customer, can protect users and data wherever they are. That’s something that’s impractical – if not impossible – to do today with on premise security alone, regardless of how good it is.
Enea
You’re right that the move to the cloud has really already happened, and the coronavirus pandemic greatly accelerated the shift. The transition to remote work also led to a spike in the number of employees using both business and personal devices to connect to corporate resources. Should organizations try to stop the use of personal devices across their networks? How should they manage the risks that this creates?
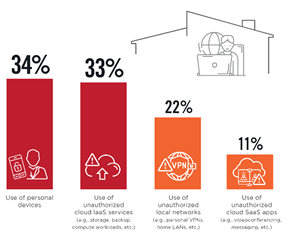
The use of personal devices was the work from home (WFH) IT practice that generated the most concern with respect to security
J.G.
The first thing I would say is that you will never be able to “stop” the use of personal devices.
Secondly, no matter what emergency situations organizations had planned for prior to 2020, even the best companies didn’t foresee that a majority, and in some cases, 100% of their employees would suddenly be remote overnight. And worldwide, that’s what happened when the coronavirus pandemic broke out.
The irony is that in many technology companies like Netskope, where I work, we didn’t even miss a step because most of our employees were already working remotely at least part of the time. But this wasn’t the case for everyone. In our conversations with customers, even large global consulting organizations, we were told that when the pandemic broke out and all the employees were sent home, they were working 24 hours a day trying to help people get connected, and people were using anything they could because the companies didn’t necessarily have devices or reliable secure connectivity for everyone.

Also, the reality is, the technology exists to help people, so personal devices are going to be part of our work in the future, no matter what. That might be a tablet, or a laptop, or your grandmother’s computer, it doesn’t matter what it is, people will use whatever is available. But it doesn’t mean you can’t provide security. There are many technologies for this, from using a reverse proxy, or browser isolation to routing people through secure systems. There are plenty of technologies that can help provide this kind of security, so people shouldn’t think we can’t use personal devices.
The other thing is, and it’s glossed over by so many people and so many corporations, people using personal devices for work need to know what kind of use is acceptable. It sounds simple, but training, communication, education, and having a policy for your employees is essential. It has nothing to do with technology, so people overlook it and don’t understand the importance of it.
It’s also very important to keep in mind that your average user doesn’t know a lot about computer security. They may not be trying to be malicious on purpose, but that doesn’t stop them from being an accidental malicious user. You need to account for that with technology. Remember, security is not the day job for most people. They’re not computer security professionals, they’re just doing their regular jobs.
Enea:
And what about the use of business devices in a home environment? Does the use of business devices in a home environment introduce risk, and if so, what kind of risk?
J.G.
Well, from our perspective, I think there’s a real risk from consumer IOT products, when you are using a corporate device such as a laptop in a home environment. So, let us imagine there can be an incorrectly patched device such as your Alexa assistant, which is connected to the corporate PC via the home environment. It’s got some malware from the home network and it infects this PC.
This PC when connected, even via VPN, to the corporate network, could be a source of infection by sending malware onto the network and premises. So this is, from our perspective, an important concern and has to be taken into account when people are bringing corporate laptops or corporate equipment into their home environment. These devices are not only connecting to the VPN and the corporate network, they are also connecting to the devices which are present in the home environment.

Security managers should also keep in mind the fact that lots of IOT devices have inherently insecure default usernames and passwords that are well known, so the devices are compromised very easily. People need to write policies for this, such as restricting their MAC address, because it’s impossible to do authentication on most IOT devices, which were not built with advanced security in mind. It can very technical, but organizations need to address this issue because a lot of IOT devices are very, very insecure by default. It’s something people should be worried about.
Enea:
Another risk on the minds of most is malware. According to the Cloud/SaaS security survey, malware infection via connected devices is the cloud risk which concerns security professionals the most. The cloud is seen as a major malware injection vector.
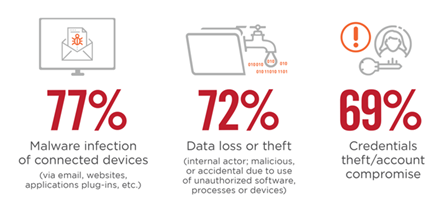
Saas-related threats that generate most concern
Does this correspond to what you are seeing in the field? Are malware incidents on the rise?
J.G.
Yes, of course they are. And the reason is the use of the cloud is on the rise. The people who create malware and other attack vectors are simply looking at how people are working. They see that everyone is accessing Office 365, G-suite, Box, Dropbox or Salesforce.com and these become the new attack surface, the new attack vectors. More than that, people writing malware have now started to place part of the malware in the cloud.

So, when a user gets infected, it may be with something very small, but it calls out to the cloud, to an authorized cloud application. If they figure out that a company is using Box, or Dropbox or Office 365, for example, the malware will reach out to download from that authorized cloud application. This is why it’s so important that even if you allow, for example, Office 365, you only allow corporate instances of Office 365, and not personal instances. And, of course, the same methodology applies to Box and G-Suite, etc. There are corporate versions of all these applications, or instances, and there are personal instances. This is so important because the technology exists (at Netskope, for example) that can differentiate between the two and block all personal instances.
So even if the attack surface changes or the malware changes, you’re not powerless, you’re not helpless. The technology already exists to help you with this. It enables you to protect your networks and prevent damage by differentiating corporate vs personal instances and monitoring where malware may be stored and then, in real-time, inspecting the traffic, whether it’s an upload or a download, whether it’s encrypted or not, but to inspect it and stop the malware threats in real-time.
So to conclude the first part of this interview, it seems that cloud resources, the use of personal devices for business, the at-home use of business devices, and the rapid expansion of IoT devices are already part of most organizations’ working environment. They all bring with them certain risks. The good news is that there are technical processes and tools available to manage these risks. And there are companies, such as Netskope, that have the expertise and experience to implement them.
In part 2, Joe will discuss the risk of data loss, the role of SD-WAN in contemporary networking, and investment strategies for ensuring security in a direct-to-Net/direct-to-cloud world.
The post Cybersecurity for a Cloud-First, Work-from-Home World appeared first on Cybersecurity Insiders.
February 17, 2021 at 03:16AM






0 comments:
Post a Comment