The cognitive tools/technologies of machine learning (ML) and artificial intelligence (AI) are impacting the cybersecurity ecosystem in a variety of ways. Applied AI machine learning and natural language processing are being used in cybersecurity by both the private and public sectors to bolster situational awareness and enhance protection from cyber threats. The algorithmic enablers that make ML and AI pinnacles of cybersecurity are automation and orchestration.
Last year, the research and analyst firm Gartner created a term called SOAR. It stands for Security Orchestration, Automation and Response. A key element of SOAR has been the automation and orchestration elements. An excellent analysis of the impact of automation was provided by Stan Engelbrecht in his column in Security Week called The Evolution of SOAR Platforms.
Stan noted “as SOAR platforms evolve, they are requiring less experience from users. Vendors embed security expertise into the products, in the form of pre-built playbooks, guided investigation workflows, and automated alert prioritization.
Automation and orchestration features have also reached a level of sophistication where they can be integrated into an existing security framework without relying on users to know exactly what should be automated.”
Indeed, SOAR and corollary cybersecurity automation technologies combined with ML and AI tools can be viewed as a strong framework for mitigating evolving threats. AI and ML have emerged into new paradigms for automation in cybersecurity. They enable predictive analytics to draw statistical inferences to mitigate threats with fewer resources. In a cybersecurity context, AI and ML can provide a faster means to identify new attacks, draw statistical inferences and push that information to endpoint security platforms.
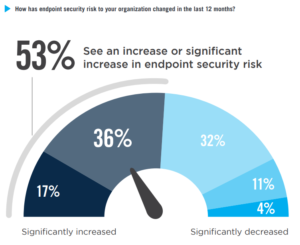
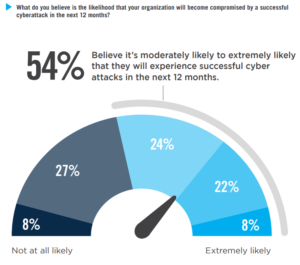
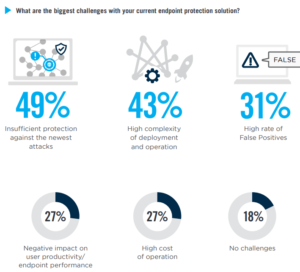
Three significant factors are heightening their risk:
1) Skilled Worker Shortage: It is widely noted that the cybersecurity industry is facing major skilled worker shortages. According to data published on Cyberseek, U.S. employers in the private and public sectors posted an estimated 313,735 job openings for cybersecurity workers between September 2017 and August 2018. That’s in addition to the 715,000-plus cybersecurity workers already employed. It is not just a U.S. problem, but a global problem and the demand for skilled workers to address the growing prevalence and sophistication of cyber-threats is growing exponentially.
2) Expanding Digital Connectivity: The expanding connectivity of the Internet of Things (IoT) has greatly increased cyber vulnerabilities. IoT refers to the general idea of devices and equipment that are readable, recognizable, locatable, addressable, and/or controllable via the internet. This includes everything from home appliances, wearable technology and cars. Gartner predicts that there may be nearly 26 billion networked devices on the IoT by 2020. The numbers of devices provide a larger attack surface with more targets for cyber criminals and makes defending networks and endpoints even more difficult.
3) Sophistication of Adversaries: Cybersecurity criminals are using machine learning techniques to discover vulnerabilities on their targets and to automate their own attacks (with increasing success). They often share tools available on the Dark Web and hacker attacks are now faster, more calculating, and more lethal. The threat actors are many and varied including nation states, criminal enterprises, and hacktivists.
The three factors I highlighted are not the only ones forcing the need for automation and orchestration tools, but they are prevailing ones. To keep up with cyber-threats and help level the playing field against attackers, companies and governments need to evaluate and assimilate many of the automation and orchestration tools that hackers employ and integrate them into their own Security Automation and Orchestration (SOAR) platforms and security information and event management (SIEM) platforms. They should implement these tools and technologies under a comprehensive risk management strategy.
Security automation and orchestration of applications should be commensurate and grow with derived benefits (and adversarial risks) from AI and ML. These technologies can provide for more efficient decision-making by prioritizing and acting on data, especially across larger networks and supply chains with many users and variables.
The automation and orchestration tool chest can now utilize horizon scanning technologies, filter through alerts, use predictive analytics, facilitate identity management, coordinate incident response (audits and alerts), use self-repairing software and patch management, and employ forensics and diagnostics after an attack. Automation and orchestration can be valuable in enhancing existing cybersecurity architecture such as preventive security controls, including firewalls, application security and intrusion prevention systems (IPSs). Perhaps most importantly, automation and orchestration can provide a more rapid response capability across a multitude of security components and tools whether they are located in the Cloud or in onsite data centers. The faster a CISO can identify and address a threat or breach, the better the likely outcome.
Combating machine-driven hacker threats requires being proactive by constantly updating and testing cybersecurity capabilities. Using ML automation platforms to recognize and predict anomalies associated with the data-base of behavioral patterns of malicious threats can be an indispensable layer in an integrated cyber-defense.
For the public sector, automation, combined with ML and AI, is an emerging and future cybersecurity pathway, especially for industrial systems and critical infrastructure.
DARPA is investing for the Department of Defense (DoD) in developing these capabilities for the warfighter. DARPA announced a multi-year investment of more than $2 billion in new and existing programs called the “AI Next” campaign. DARPA’s website notes that “key areas of the campaign includes automating critical DoD business processes, such as security clearance vetting or accrediting software systems for operational deployment; improving the robustness and reliability of AI systems; enhancing the security and resiliency of ML and AI technologies; reducing power, data, and performance inefficiencies; and pioneering the next generation of AI algorithms and applications, such as “explainability” and “common sense reasoning.”
For domestic federal security, the Department of Homeland Security (DHS) has deployed an automated cyber surveillance system that monitors federal internet traffic for malicious intrusions and provides near real-time identification and detection of malicious activity called EINSTEIN. This system is continually being upgraded.
Einstein is only one element of DHS’s use of automation. DHS’s newly created Cybersecurity and Infrastructure Security Agency (CISA) will be using cognitive automation for cyber, collaboration and communication capabilities in many areas of its defined mission:
Proactive Cyber Protection
- CISA’s National Cybersecurity and Communications Integration Center (NCCIC) provides 24×7 cyber situational awareness, analysis, incident response and cyber defense capabilities to the Federal government; state, local, tribal and territorial governments; the private sector and international partners.
- CISA provides cybersecurity tools, incident response services and assessment capabilities to safeguard the ‘.gov’ networks that support the essential operations of partner departments and agencies.
Infrastructure Resilience
- CISA coordinates security and resilience efforts using trusted partnerships across the private and public sectors, and delivers training, technical assistance, and assessments to federal stakeholders as well as to infrastructure owners and operators nationwide.
- CISA provides consolidated all-hazards risk analysis for U.S. critical infrastructure through the National Risk Management Center.
Emergency Communications
- CISA enhances public safety interoperable communications at all levels of government, providing training, coordination, tools and guidance to help partners across the country develop their emergency communications capabilities.
- Working with stakeholders across the country, CISA conducts extensive, nationwide outreach to support and promote the ability of emergency response providers and relevant government officials to continue to communicate in the event of natural disasters, acts of terrorism, and other man-made disasters.
Cybersecurity Ventures predicts that cybercrime will cost the world $6 trillion annually by 2021. That is a scary scenario. It is important that both government and industry are investing together in automation and orchestration to harness productivity and to especially address cyber-threats. It will take a vibrant partnership to help meet the threats. With every passing year, cyber criminals become more sophisticated and adept in their cyber-attacks. In view of a lack of skilled workers, expanding digital connectivity, and the growing sophistication of adversaries, automation and orchestration are key elements for a viable cybersecurity posture. Ultimately, incorporating these elements will become a cybersecurity imperative in an AI and ML guided world.

The post Security Orchestration, Automation and Response (SOAR) – The Pinnacle For Cognitive Cybersecurity appeared first on Cybersecurity Insiders.
November 27, 2018 at 09:10PM


















 ). Let me know in the comments or by tweeting us
). Let me know in the comments or by tweeting us