[Jacqueline Faerman, PR Manager, Privacy Bee]
In 2024, many organizations operate with a newly expanded attack surface. Even though most already invest significantly in cybersecurity. All companies are acutely aware of the threat posed by cyberattacks and the resulting data breaches. And sadly, many have already been victimized. If they wish to avoid being breached, CEOs, CFOs, CHROs, and all other non-IT department heads must become educated about how and why their organization’s attack surface has been expanded. Cyber threats have evolved into business threats; every department should be vigilant. Once they do, they will undoubtedly want to address the challenges of shrinking the attack surface immediately. This document will shed light on the attack surface and what can be done to minimize it – even if an organization already invests significantly in information security.
If you’re a CFO, CEO or other organizational leader not directly involved with information security and IT, you may not often hear the term “attack surface”. So, here’s a basic definition of the term.
An organization’s attack surface is defined as all the possible points of entry a cybercriminal might exploit to gain unauthorized access to information systems. This includes every endpoint – e.g., mobile device, desktop, server, web applications/software, APIs, etc. – and other potential vulnerability to cyberattacks or data breach attempts.
Most modern organizations have a sprawling attack surface because information systems, computing networks and cloud hosting/storage have become so integral to the operations of every industry. There are generally two classifications or subsets of attack surfaces in a broad sense. Chief Information Officers or Chief Information Security Officers know they must apply different strategies to secure the digital attack surface as well as the physical attack surface. And many have been working for years to reduce their exposure.
The physical attack surface is comprised of all the hardware that hackers might try to infiltrate. These are all your organizations’ endpoint devices such as desktop computers and workstations, mobile devices, phones, tablets, even USB drives and other portable storage devices. Remember that when retiring old hardware, the discarded devices may still contain log in credentials, passwords, sensitive user or organizational data or more. To a lesser extent the physical attack surface also includes protecting actual physical locations from intruders who could sneak into facilities and steal data manually. To shrink the physical attack surface, InfoSec leaders implement hardware management policies and other common endpoint security measures.
The digital attack surface is more difficult to defend because it is distributed across the internet. It is comprised of software systems, applications, websites, servers, email systems, cloud storage/hosting, and unauthorized system access locations. Digital information security is largely focused on closing holes and other vulnerabilities that arise from poor coding, insufficient passwords, weak encryption, open APIs, outdated software, etc.
The goal of any organization is to shrink, to the smallest extent possible, their physical and digital attack surfaces to guard against unwanted public access to sensitive data.
The New Social Engineering Attack Surface
In recent years a new attack surface has emerged, and it is clearly undermining the efforts of IT and InfoSec leaders to protect their organizations. This new attack surface has been dubbed the “Social Engineering Attack Surface”. For organizations that had successfully shrunken their digital and physical attack surfaces, the rise of social engineering attacks has exploded the scope of potential attack vectors and breaches are on the rise.
Social engineering can straddle digital and physical attack vectors and leverage unregulated external data available for sale or even for free on the public internet. This article from Privacy Bee details the methods cybercriminals use to exploit weak external data privacy in social engineering attacks.
While physical and digital attack surface management involves a fairly concrete set of processes and best practices, social engineering attack surface management presents a more slippery challenge. CISOs, CIOs, and InfoSec professionals can exert robust control over the digital and physical assets under their supervision and purview. By contrast, social engineering attacks are not directed at surfaces under the organization’s direct control. Instead, social engineering attacks are directed toward any or every member of the organization’s workforce. Social engineering attacks also regularly target the workforce elements of an organization’s vendors, third-party associates, supply chain partners and any external group that has systems integrations with the organization. InfoSec leadership has far less ability to control the online activities of all these persons. And it is the human element that hackers exploit. This is why the social engineering attack surface is so much more difficult to reduce.
Finding the Shortcomings in Existing Attack Surface Management Practices
Respected B2B technology vendor marketing firm TechTarget published an overview of the steps involved in creating a risk mitigation plan. To summarize, there were five recommendations:
-
Identify the risk – catalog existing and potential events and event sequences where risk is inherent. Whether from existing vulnerabilities or known threats against the organization
-
Perform risk assessments – using a weighted system to determine the possible impact of each risk and how likely it is to occur.
-
Prioritize – ranking the potential risks identified in the assessment and acting first on the areas with the lowest acceptable risk.
-
Track risks – this involves an ongoing monitoring of risks identified and noting the frequency of attacks in different types of risk pools.
-
Implementing mitigation and monitoring progress – Once a risk mitigation plan has been developed and deployed to address the risks identified and prioritized in the earlier steps, the organization should monitor the efficacy of the plan, keep tabs on the threat levels, and make modifications to the plan as the priorities may shift.
The five recommendations from Tech Target are well-conceived and if applied, should serve well to reduce the size of any organization’s attack surface. But this is only if the organization is savvy enough to use it to the new social engineering attack surface. Evidence suggests this is not yet happening across the preponderance of organizations in the US.
In 2022, leading tech research and advisory firm Gartner predicted the expansion of the attack surface driven by the dispersal of enterprises (by expanded remote work arrangements, further supply chain diversification, and other causes). At the time of their prediction, Gartner estimated information security spending would reach $172 billion in 2022. In 2023, Gartner expects $188 billion will be spent. US organizations are willing to spend mightily to combat the risk of cyberattacks. However, simply throwing money at the problem will not suffice.
The shortcomings in contemporary efforts don’t lie in the spending level directed toward the problem. Instead, the problem is that organizations are not applying the above five risk mitigation steps properly to the specific risks of social engineering strategy. To successfully shrink the social engineering attack surface, InfoSec leaders must understand that the risks of social engineering attacks originate, on average, a full YEAR before the attack is perpetrated.
When performing TechTarget’s “step 1” (risk assessment), one cannot simply focus on “intrusion attempts” as the inception of the risk. However, that is precisely what the current Physical and Digital attack surface management strategy dictates.
To interrupt social engineering attacks and shrink the social engineering attack surface, organizations need to adopt a forward-looking, preemptive posture toward risk assessment. They must focus on external data privacy and external data hygiene practices.
In the article “The Anatomy of Spear Phishing Attacks” published by Privacy Bee, the typical cyber attack process is detailed in a step by step process. Illustrated in the graphic below, is a clear characterization of the breadth of the attack surface currently exposed for most organizations.
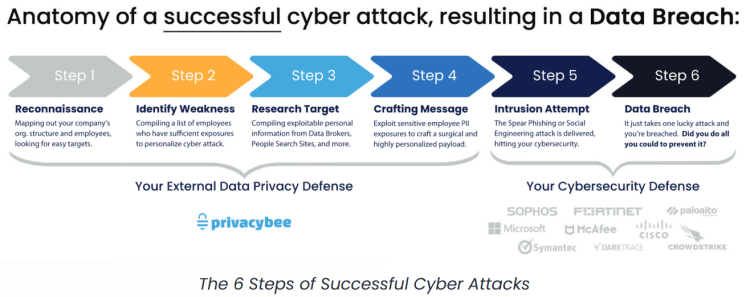
Today’s mainstream strategies for attack surface management only address steps five and six. So, it becomes easy to see that steps one through four represent a social engineering attack surface some 66% larger than is acceptable.
When performing the risk identification process – or Step 1 in the TechTarget Attack Surface Management process – it is essential to identify unsecured external data as the primary risk.
External Data Privacy expert, Arnez Edwards of Privacy Bee explains, “If external data privacy is left wholly unaddressed, cyber criminals and other threat actors are allowed to reconnoiter and map out your company’s organizational structure. They can identify the appropriate targets within the workforce (and vendor/affiliate workforce) to determine which workers have appropriate access to the data and systems the criminals want to attack.” These are steps one and two in the Anatomy of a Successful Cyber Attack graphic – Reconnaissance and Identification of Weaknesses. The reconnaissance is often as simple as visiting the target organization’s website and reading the information about the company, its executives, its locations, business partners, and business activities.
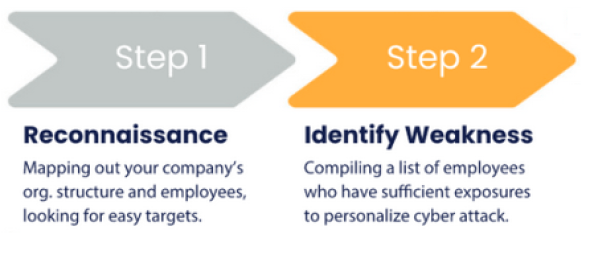
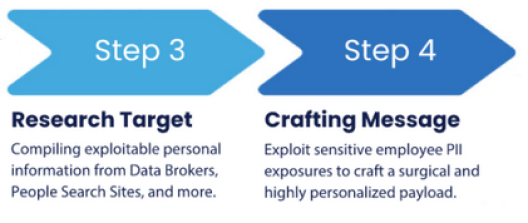
Step three in the anatomy graphic is “research target”. This is where, according to Edwards, “the gaping hole of external data privacy represents an unacceptably large attack surface” for many organizations. Using resources such as People Search Sites, Data Broker firms, search engines, and social media profiles, bad actors can glean highly specific information about their targets. Whether they purchase personally identifiable information (PII) from data brokers or simply scrap PII from social sites like LinkedIn, Facebook or others, compiling PII about identified targets helps hackers prepare for step four – crafting the message for social engineering attacks.
For detailed examples of how cybercriminals craft messages for different flavors of social engineering attacks, review Privacy Bee’s article titled, “Spear Phishing Attacks: Types, Elements, and Detection”. With detailed personal information about a specific employee/target’s life and recent activities, creative hackers and cybercriminals can produce a broad array of attacks like Spear Phishing, business email compromising, whaling and credential harvesting, etc.
Also, note the imbalance between defenses applied to steps five and six in the Six Steps of a Successful Cyber Attack graphic. This additionally illustrates the unprotected attack surface posed by social engineering risk. The graphic clarifies that organizations have processes and practices to address the physical and digital attack surface. It also clarifies where organizations must focus efforts to shrink this new and significant attack surface.
External Data Privacy Management Shrinks the New Attack Surface
Managing and protecting access to the PII of every single employee and those of all third-party affiliates (like vendors and other partners) may seem like an overwhelming challenge. Knowing 350+ People Search Sites and data brokers, dozens of social media platforms, powerful search engines, and tons of publicly searchable data makes it an even more sobering prospect. However, as Arnez Edwards says, “You can’t sit around waiting for defenses to fail. You must act on the offense and disrupt attacks before they start. Utilizing data privacy platforms, such as Privacy Bee, can help shrink the attack surface back to acceptable tolerances through multiple methods:
Understanding and Shrinking Attack Surfaces: A Comprehensive Guide for Organizational Leaders
In the ever-evolving cybersecurity landscape, the concept of attack surfaces has become increasingly crucial for organizations to comprehend and address. Despite significant investments in cybersecurity measures, expanding attack surfaces has left many companies vulnerable to cyber threats and data breaches. As organizational leaders, it is imperative to understand what attack surfaces entail and how they can be minimized to mitigate risks effectively.
What is an Attack Surface?
An organization’s attack surface encompasses all potential points of entry that cybercriminals might exploit to gain unauthorized access to information systems. This includes various endpoints such as mobile devices, desktop computers, servers, web applications, APIs, and more. Modern organizations face a sprawling attack surface with the integration of information systems, computing networks, and cloud hosting/storage into everyday operations.
Types of Attack Surfaces
Attack surfaces can be broadly classified into two categories: physical and digital. The physical attack surface comprises hardware devices susceptible to infiltration, including desktop computers, mobile devices, and USB drives. It also extends to physical locations, necessitating protection against intruders who might attempt to steal data manually.
On the other hand, the digital attack surface presents a more complex challenge as it is distributed across the internet. It encompasses software systems, applications, websites, servers, email systems, and cloud storage/hosting. Securing the digital attack surface requires addressing vulnerabilities arising from coding flaws, weak passwords, outdated software, and other factors.
The Emergence of the Social Engineering Attack Surface
Recently, the “Social Engineering Attack Surface” emerged. This phenomenon has significantly expanded the scope of potential attack vectors, leading to a surge in data breaches. Social engineering attacks leverage external data available on the internet to manipulate individuals into divulging sensitive information or performing actions that compromise security.
Unlike traditional attack surfaces, social engineering attacks target the human element within organizations, making them particularly challenging to defend against. Hackers exploit unregulated external data sources to gather detailed information about targets, enabling them to craft sophisticated attacks such as spear phishing and business email compromise.
Shortcomings in Attack Surface Management Practices
While organizations allocate substantial resources to combat cyber threats, many need help managing attack surfaces effectively. Contemporary strategies often overlook the risks posed by social engineering attacks, focusing primarily on traditional physical and digital surfaces. As a result, organizations fail to adopt preemptive measures to mitigate social engineering risks, leaving them vulnerable to exploitation.
Shrinking the Attack Surface with External Data Privacy Management
Organizations must adopt a proactive approach to attack surface management to address the evolving threat landscape, particularly concerning social engineering risks. External Data Privacy Management is a critical strategy for shrinking attack surfaces and safeguarding sensitive information.
Privacy Bee offers comprehensive solutions to assist organizations in managing external data privacy effectively. Their Employee Risk Management (ERM) solution provides visibility into external privacy risks by scanning hundreds of sources for potential exposures. Similarly, the External Data Privacy Audit (EDPA) and Vendor Risk Management (VRM) tools offer insights into privacy vulnerabilities and enable organizations to mitigate risks efficiently.
By leveraging Privacy Bee’s solutions, organizations can protect employee and vendor data from exposure on the internet, thereby reducing the attack surface and enhancing overall cybersecurity posture. Additionally, engaging with Privacy Bee fosters a culture of data privacy within organizations, making them more resilient to cyber threats and attractive to prospective customers.
Conclusion
Understanding and shrinking attack surfaces are paramount for organizational leaders safeguarding sensitive information and mitigating cyber risks. By comprehending the intricacies of attack surfaces and implementing proactive measures such as external data privacy management, organizations can bolster their defenses against evolving cyber threats. Collaborating with trusted partners like Privacy Bee empowers organizations to stay ahead of adversaries and foster a robust cybersecurity posture in an increasingly digital world.
The post Understanding and Shrinking Attack Surfaces: A Comprehensive Guide for Organizational Leaders appeared first on Cybersecurity Insiders.
March 30, 2024 at 07:24AM










