By Jessica Day – Senior Director, Marketing Strategy, Dialpad
The world of IT security is complex and changeable. Recently, many companies have adopted, and continue to carry out remote working, increasing internet use, and further technical vulnerabilities for cybercriminals to exploit.
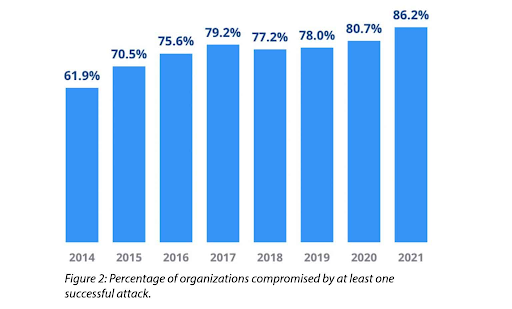
According to the FBI, cyber threats have tripled to 3,000 per day. Small and medium-sized businesses (SMBs) are most vulnerable to attack because they don’t have the resources to purchase advanced security tools.
With a 50% increase in cyberattacks year on year, it’s becoming progressively tasking and expensive for a business to protect their systems from threats like malware, ransomware, phishing, and data theft.
An effective cybersecurity infrastructure is vital to protect networks and data. However,security as a service can offer an affordable and convenient solution that meets your needs.
What is security as a service?
Security as a Service (SECaaS) is cloud-based software that provides the tools and services you need to create a robust, tailored cybersecurity solution.
Outsourcing your IT security to a third-party provider for a monthly subscription removes the need for in-house cybersecurity personnel and infrastructure.
Do not confuse SECaaS with software as a service. SaaS provides cloud-based software solutions, but if you want a complete guide to SaaS content strategy look elsewhere. SECaaS deals exclusively in cybersecurity services.
What are the benefits of SECaaS?
It can be difficult choosing between cloud-based on on-premise solutions. However, several benefits should be considered when planning your IT security. Let’s take a look.
1. Expertise
For IT security to be effective, it needs to be managed by experts. With SECaaS you’ll have access to professionals with the knowledge and experience to handle your cybersecurity requirements without having to put them on the payroll. They’ll also have access to the most up-to-date tools and equipment available and will receive training on all the latest developments and threats.
2. Comprehensive security package
A SECaaS package will provide you with instant access to the latest and most advanced security tools that will be tailored to meet your company’s needs. Many providers allow you to combine different software to create a comprehensive package.
Most SECaaS providers offer varied pricing tiers, so you only pay for what you need.
3. Save resources
Having IT experts on your payroll is expensive. In-house security teams also require regular training, plus continuous investment in hardware and software which will also need to be regularly monitored and updated.
SECaaS offers a long-term, cheaper alternative.
Let’s not forget the time and labor costs involved with running cybersecurity. Using SECaaS frees up IT teams to focus on other tasks such as maintaining endpoint hardware, or answering questions from colleagues about the best voice recorder for meeting minutes.
Plus, there are also the associated costs if things go wrong. On average SMBs $85,000 to cyberattacks. This can be in the form of penalties, operational downtime, and damaged assets.
4. Automation
Cybercriminals don’t take time off, so neither should your cybersecurity solution.
SECaaS offers protection 24/7. You’ll get around-the-clock service that monitors for vulnerabilities and potential threats, provides automatic updates for the best protection, has prompt alert systems, and offers faster responses.
There’s no need to worry about alerts being missed over the weekend, followed by a delayed response which then allows a minor threat to then become a serious problem. SECaaS offers peace of mind that your cybersecurity is always on the job protecting your system from threats like ransomware.
5. Reporting
As well as automated responses, SECaaS provides regular analysis and reporting regarding the status of your security.
Collecting, analyzing, and correlating data from various systems and applications is a time-consuming and complex task for your IT team. SECaaS removes this headache and provides accurate, organized, and actionable security intelligence that can be used to help you make informed decisions regarding strategic planning.
6. Compliance
Increased use of the internet has brought with it additional regulations which can’t be ignored. If that were not difficult enough, regulations can vary across industries and countries.
Ensuring your company is compliant with the relevant standards and regulations can be a minefield, especially when it comes to cybersecurity.
With SECaaS you can be confident you have the correct policies and procedures in place that inform appropriate solutions and are applied and constantly reviewed for any possible risks and breaches.
What SECaaS solutions are available?
There are varied and vast solutions available depending on your company’s needs. Let’s look at some of the most popular.
Network security
IT networks are high risk and complex due to multiple users and endpoints.
SECaaS provides tools that constantly monitor incoming and outgoing traffic, searching for risks and assessing threats before they occur. It can also limit access to high-risk websites.
Endpoint protection
Endpoints include laptops, mobile phones, servers, anything staff members are using to log onto your network. They’re a particular risk because they harbor several weak points that cybercriminals can exploit.
Anti-virus software is the most common endpoint protection, but SECaaS offers that and more with endpoint detection and response tools.
Data protection
Data protection is non-negotiable these days.
Data loss can cause significant disruption to operations and lead to considerable fines. SECaaS provides the tools to protect data and prevent loss or theft through constant monitoring and security checks.
Loss of customer data can be devastating to a company’s reputation. If you want to reduce customer acquisition cost, it’s vital that you protect their data from loss or theft and thereby retain customers who have confidence in your ability to keep their data safe.
Access management
Imagine you use a contact center as a service (CCaaS) provider to run your cloud-based contact center. Depending on the size of your business, you may have any number of employees logging in to your network at different times. How do you manage who can see specific areas of your system and avoid unauthorized access?
SECaaS provides cloud security access to agents to enforce your security procedures. It also offers intrusion protection that identifies and recognizes unusual activity and prevents unauthorized access.
You can also choose Single Sign-On tools to allow access to all your company applications and software with one set of credentials. This tool also provides a greater ability to monitor usage.
Email and web security
Poor email and web security can lead to malicious ads, phishing, and spam simply because it involves a lot of incoming and outgoing data. SECaaS solutions will block potentially dangerous emails and attachments before they can be opened and threaten your system.
You can also protect your websites and applications from malware and viruses that can potentially spread to any visitor or user endpoints by continuously checking the security of application program interfaces.
Security assessments
Once your SECaaS solution is up and running it doesn’t end there.
Cybersecurity is ever-changing, so you need to constantly monitor, review and adapt your package to keep up. Just like testing metrics, the package needs to be analyzed so it can be improved.
Most SECaaS packages offer ongoing security analysis that monitors for vulnerabilities, fixes bugs, identifies new threats, and provides real-time information that can help improve response times and reduce risks.
How to choose the right SECaaS provider for you
Outsourcing IT security to a third party requires careful consideration.
Before you start, it’s important to identify your company’s needs, then select the provider that can meet them.
When you’re ready to delve into the selection process you should consider the following points.
Availability
The reason you’ve opted for SECaaS is to provide 24-hour protection for your IT system. You, therefore, need a provider that responds around the clock.
Providers should be able to deliver a guaranteed response time for incidents, queries, and system updates.
Service loan agreement
Always check the service loan agreement meets your needs. It should outline the services provided, the available support, agreed response times, service fees, and any consequences for the provider due to non-compliance.
Varied pricing/scalability
You should not have to pay for services you do not need. Ensure your provider has varied pricing options and the opportunity for scalability. If your company grows you will need your cybersecurity package to grow with it and a flexible provider is essential.
Provider credentials
A little research can go a long way to help you choose your provider with confidence. You may use conversion funnel metrics to help you understand your customer’s journey from consideration to purchase. As you follow this process to choose your provider, check they deliver the service standards you expect from start to finish.
Verify their credentials. Do they have the required certifications? Do their staff have the correct qualifications, knowledge, and experience?
Check them out with other service end-users. Their feedback may provide insight you never considered.
Takeaway
Choosing to transfer your IT security to a cloud-based third party can be daunting, but there are plenty of benefits.
Such a decision depends upon the size of your company and its needs. Choosing SECaaS can make a complex task much simpler in the rapidly changing world of cybersecurity.
If you’re an email service vendor who wants protection from phishing, or a school, you want reliable, convenient, and affordable cyber protection. SECaaS can provide you with a varied and tailored package to meet your needs and reduce the workload of your internal IT team.
Bio:
Jessica Day – Senior Director, Marketing Strategy, Dialpad
Jessica Day is the Senior Director for Marketing Strategy at Dialpad, a modern business communications platform that takes every kind of conversation to the next level—turning conversations into opportunities. Jessica is an expert in collaborating with multifunctional teams to execute and optimize marketing efforts, for both company and client campaigns. She has also written for sites such as VirtualSpeech and Globalization Partners. Here is her LinkedIn.
The post Introducing SECaaS (Security as a Service): A Comprehensive Guide appeared first on Cybersecurity Insiders.
March 28, 2022 at 08:10PM






0 comments:
Post a Comment