Making sense of increasing amounts of complex data is a challenge in many industries. Cybersecurity professionals must manage data generated by the countless systems in your network. Feeds from disconnected, siloed tools must be normalized and analyzed so SOC teams can appropriately prioritize remediation efforts.
And that’s where RiskSense comes in. The company lauds itself as, “the industry’s most advanced and scalable platform for continuously correlating and analyzing evolving threat and vulnerability data.” Based on our product review, there’s ample evidence to substantiate this claim.
RiskSense helps cybersecurity teams advance from reactionary mode to a proactive, collaborative, and real-time cyber risk management discipline, focused on the threats and vulnerabilities that matter most. RiskSense coverage includes threat and vulnerability data for all of asset classes, including:
- Network
- Endpoint
- Application
- Database
- IoT
One Tool to Rule Them All
RiskSense provides intelligence-driven prioritization of threats and vulnerabilities. To accomplish this, the platform ingests data from a variety of security and IT tools as well as external threat data feeds and custom data sources including tools such as Network Vulnerability Scanners, Application Vulnerability Scanner , Database Security Systems, Configuration Management Systems,, and many more. RiskSense’s “Smart Connector Framework” connects to existing security and IT infrastructure using,CSV, XML, , and Web services APIs.
Ultimately, RiskSense preserves existing technology investments and enhances their value by automating the processes of data aggregation, correlation, and normalization. The result is an improved view of an organization’s security posture, enabling security teams to be more effective in remediation.
External Threat Data Adds Context
Internally collected security intelligence is contextualized with external threat data from the RiskSense Cyber Security Research Center, which is continuously monitoring the cyber space for emerging threats.
It unifies this data with threat intelligence feeds from other industry sources to provide accurate and timely threat assessments that enables valuable threat attribution and lets cyber teams focus on security gaps that are being exploited by cyber adversaries.
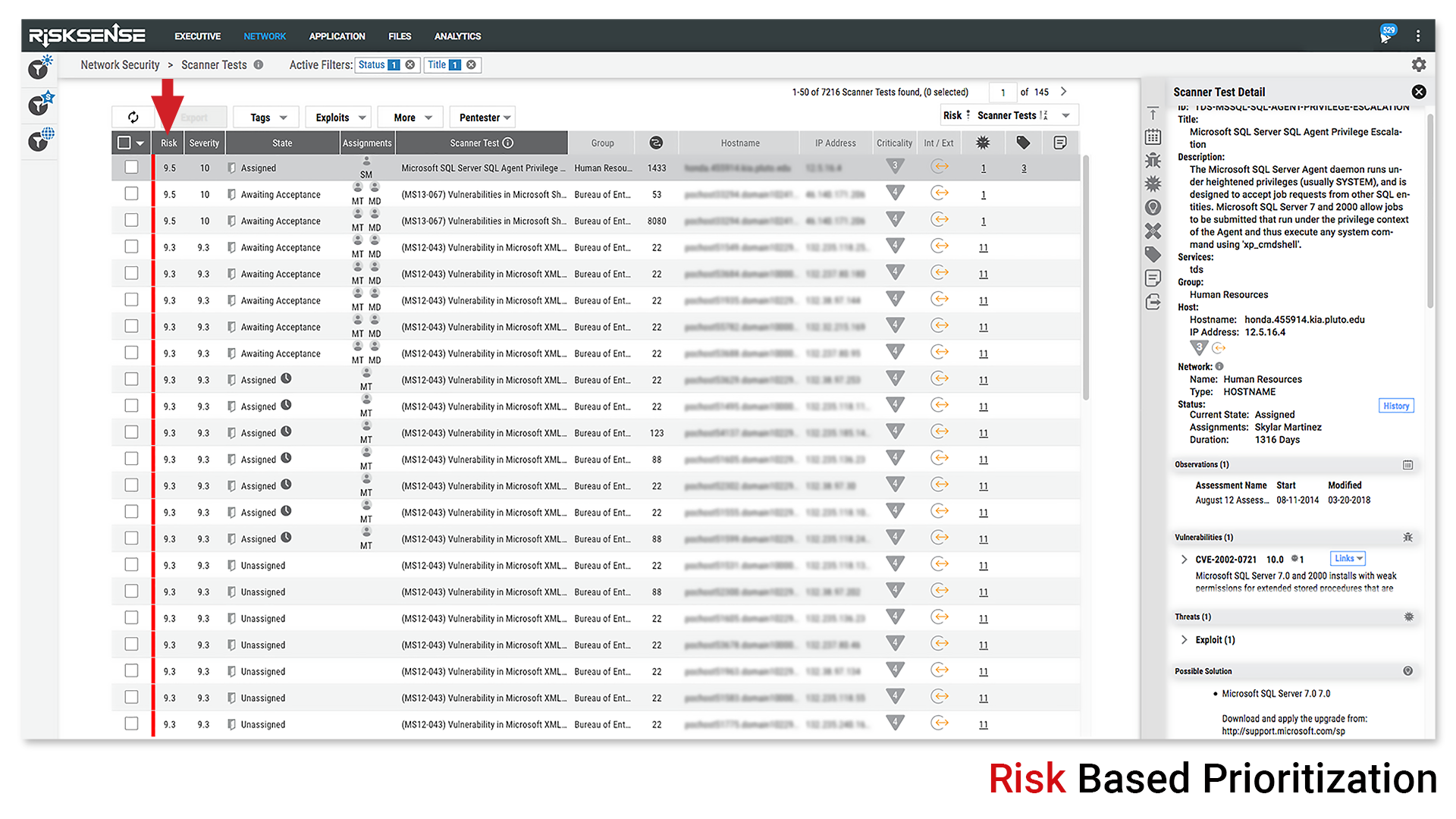
Familiar Risk Ranking Structure
In a fitting analogy, RiskSense compares cyber risk profiles to a credit score. A company’s RiskSense Security Score (RS3) ranks overall exposure to risk from 300 to 850, the same scale as is used for credit ratings. RS3 also includes a visual representation of cyber risk posture at both the organization and asset level.
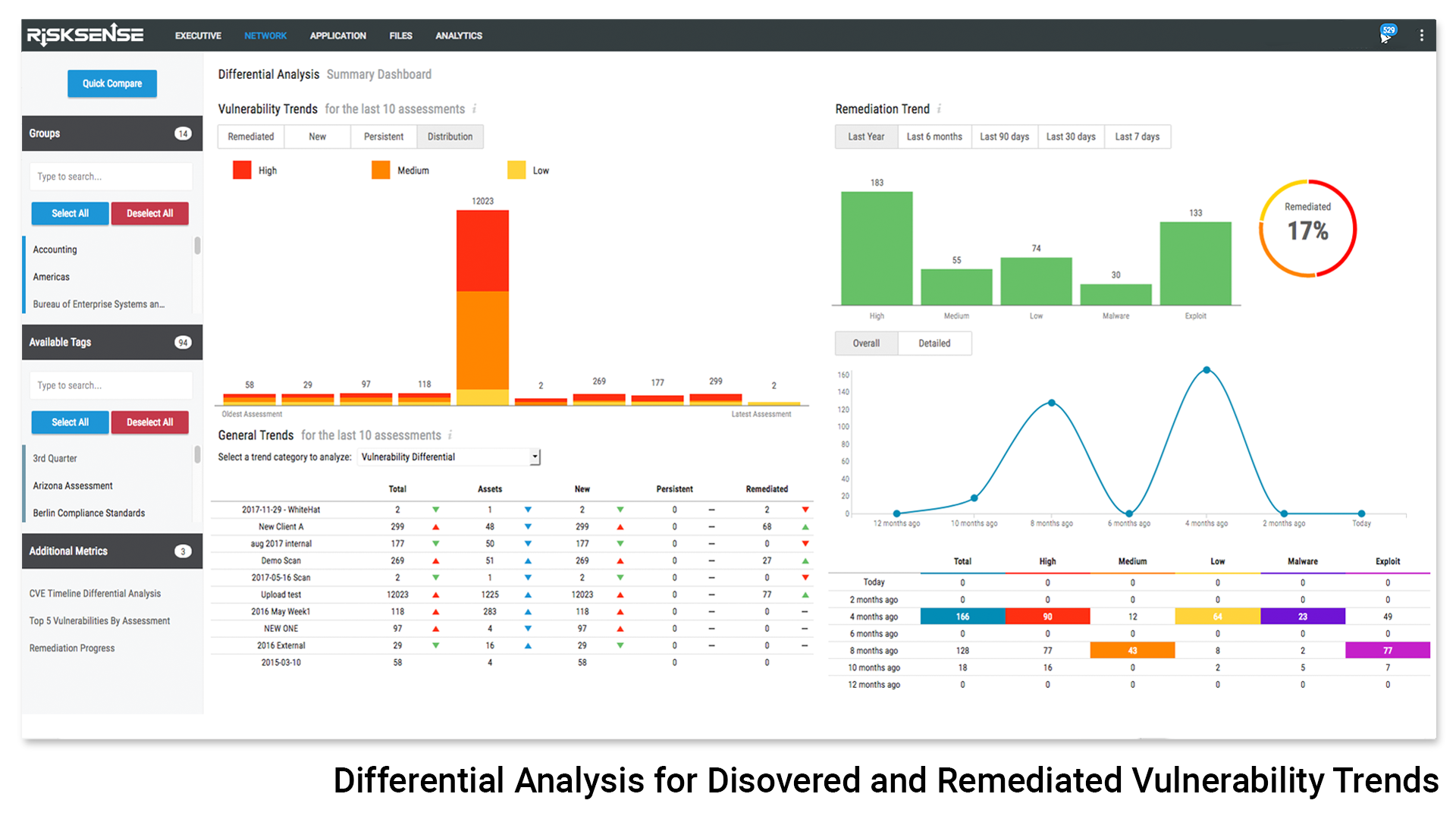
Added context helps guide remediation efforts by taking into account severity, business risk, weaponization, and active exploits using data from over 60 independent sources. The Platform also normalizes the aggregated data and minimizes false-positives by conducting differential analysis across the different sources and unifying the data to avoid duplicates and enrich the findings.
AI + Humans = Ideal Cyber Risk Management
As the attack surface of enterprises continues to grow, it’s humanly impossible to manually process the massive amounts of data continuously generated by security tools. RiskSense uses artificial intelligence to assess and prioritize vulnerabilities based on their actual exploitability, risk impact, and the IT environment.
While use cases for AI continue to expand, RiskSense acknowledges the value of the human element. Indeed, human intelligence is a part of the stated advantage. The company uses a combination of human intel and AI-assisted pen testing to validate a client’s actual susceptibility and the most likely attack scenarios. Interactive drill-down and visualizations of correlated data and application attack path analysis further empowers security operations team to see how to break the kill chain.
RiskSense also invests heavily in research. The company employs security researchers and collaborates via its Fellowship Program with leading IT and cyber security programs at various universities. Finally, RiskSense also assists human workflows with a ticketing system that helps collaboration between security and IT operations teams, thereby streamlining the remediation processes and shortening time-to-remediation dramatically.
What Customers Say
“RiskSense lets us cut the data and take a different view and really helps us prioritize what we should be working on. That’s where we really found a lot of value.”
– CISO, CenturyLink
“RiskSense is our go-to partner for cyber security. Excellent partner for consulting and work.”
– CIO, Arizona State University
“RiskSense easily sets the important information in front of the resources needed to remediate.”
– Ryan Regnier, IT Director, Nelnet.net, USA
Licensing & Pricing for RiskSense Cyber Risk Management
The RiskSense Platform is delivered as Software-as-a-Service in the AWS GovCloud and is offered as an annual subscription-based model. The SaaS platform is priced on a per-asset basis that includes any network, web application, database, or IoT devices. The annual subscription price starts at $15,000 for 1,000 assets and can be scaled up to a million assets.
Additionally, for customers that prefer to outsource some of their risk management tasks, RiskSense offers its RiskSense Vulnerability Discovery Service and RiskSense Attack Surface Validation Service.
About RiskSense
Headquartered in Albuquerque, New Mexico, RiskSense, Inc., is a spin-off of the New Mexico Institute of Mining and Technology and originally conducted research-as-a-service projects. As part of a think tank that advised the U.S. Department of Defense and U.S. Intelligence Community, RiskSense developed Computational Analysis of Cyber Terrorism Against the U.S. (CACTUS), Support Vectors Intrusion Detection, Behavior Risk Analysis of Vicious Executables (BRAVE), and the Strike Team Program.
To learn more, visit the RiskSense site and catch a weekly product demo.
The post PRODUCT REVIEW: RiskSense Cyber Risk Management appeared first on Cybersecurity Insiders.
April 12, 2018 at 12:53AM






0 comments:
Post a Comment