
On December 13 2020, multiple vendors such as FireEye and Microsoft reported emerging threats from a nation-state threat actor who compromised SolarWinds, and trojanized SolarWinds Orion business software updates in order to distribute backdoor malware called SUNBURST. Because of the popularity of SolarWinds, the attacks have affected multiple government agencies and many Fortune 500 companies. It also appeared in the recent CISA Emergency Directive 20-01.
We analyzed decoded DGA domains from SUNBURST and found 165 unique domains that were affected by the backdoor malware. Some of them might be victims, and some of them might relate to security detection or analysis such as sandboxing. We found the affected domains span across different types of organizations (including information technology, public administration, education, and finance and insurance etc.) and belong to 25 different countries (spanning to all the continents except Antarctica).
1.0 Introduction to SolarWinds Orion Supply Chain Compromise
As mentioned in the FireEye report, the SolarWinds might be attacked by a nation-state threat actor. But which one remains a mystery. Some news articles conjecture it is related to APT29 or Cozy Bear, a Russian hacker group, and the detailed evidence is not revealed.
According to SaveBreach, Security Researcher Vinoth Kumar discovered a password that belongs to SolarWinds update server has been leaked to Github since 2018. It is unclear whether the attackers have utilized the weak password in the attacks, but it shows the weakness of SolarWinds security posture.
In a report filed by SolarWinds to SEC, SolarWinds’s emails through Office 365 might have been compromised and “may have provided access to other data contained in the Company’s office productivity tools.”.
SolarWinds said as many as 18,000 of its high-profile customers might have installed a tainted version of its Orion products.
2.0 SUNBURST DGA algorithm and communication
On the network level, the most obvious IOCs related to SUNBURST are the domains used in the C2 (Command and Control) channel. It comes with a strong pattern and mimics cloud host names, e.g., 7sbvaemscs0mc925tb99.appsync-api.us-west-2.avsvmcloud.com, a DGA (Domain Generation Algorithm) domain.
The FireEye and Microsoft reports are among the first to provide technical details regarding the SUNBURST backdoor malware. From there we know, the attackers injected malicious update SolarWinds-Core-v2019.4.5220-Hotfix5.msp. Inside the update, the malicious component is SolarWinds.Orion.Core.BusinessLayer.dll.
Through analyzing this .NET DLL binary, different research groups (RedDrip and Prevasio) revealed some level of details regarding how DGA domains are encoded. The overall wisdom shows that the domains follow a structure:
${GUID:16byte}${Encoded_AD_domain}.appsync-api.${region}.avsvmcloud.com
The ${region} is in one of the four values:
- eu-west-1
- us-west-2
- us-east-1
- us-east-2
The ${GUID} part comes from a hash of host level information, so it is not easily reversible.
The ${Encoded_AD_domain} is mostly interesting, the corresponding plaintext value shows which domain the machine belongs through the .NET API call:
IPGlobalProperties.GetIPGlobalProperties().DomainName
Essentially the API returns the name of Windows Domain. Through that we can discover which company the machine belongs to.
2.1 Decode Encoded AD Domains
We leverage the research discovery from RedDrip and Prevasio, on the decoding algorithms to restore the ${Encoded_AD_domain}. Basically, the attacker employs two different decoding functions: one is a customized BASE32_decode function and another is a more customized letter replacement cipher when the domain name only has lower cases plus [0_-.]
3.0 Infected Domains Analysis
According to CRN news, SolarWinds stated that its customers included 425 of the US Fortune 500, the top ten US telecommunications companies, the top five US accounting firms, all branches of the US Military, the Pentagon, the State Department, as well as hundreds of universities and colleges worldwide.
To analyze infected domains in the SUNBURST Backdoor attack, we collected observed hostnames for the DGA domains from multiple sources. One major source is in Github provided by Bambenek Consulting, and the other major source is in Paste bin sourced from Zetalytics / Zonecruncher.
By feeding the encoded DGA domains to the decode script, we obtained a list of decoded domain names, which could have been generated by the victims of the SUNBURST backdoor attack. Following that, we made an attempt to manually map the decoded domain names to the company/organization names through Google search. We were able to map 165 decoded domain names to its company/organization name.
DISCLAIMER: It has not been verified that all the decoded domains are valid Windows domains and indeed belong to the victims. It is largely based on human judgement. Our manual mapping form decoded domain names to their company/organization names could be inaccurate.
3.1 Distribution of Victims by Industry Category
We observed that the victim companies/organizations span across different types of industries. We classified them into different categories based on the NAICS (North American Industry Classification System) from the United States Census Bureau. Their distribution by category is shown in Figure 1. From the samples we have, IT companies, Public Administration (e.g., Government) and Education Services (e.g., Universities) were affected most by the SUNBURST backdoor attack.
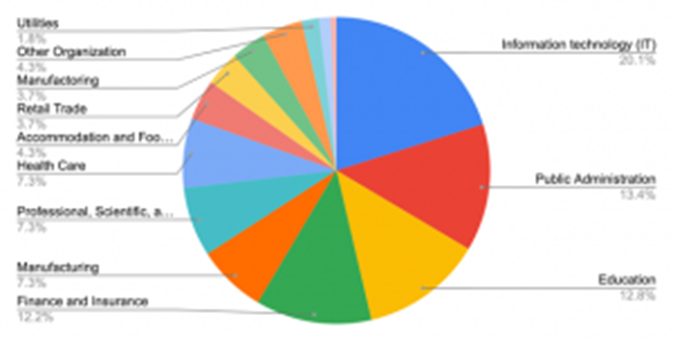
Figure 1:Victims Distribution by Industry Category.
3.2 Distribution of Victims by Country
We observed that the victim companies/organizations belong to 25 different countries. Their distribution by continent is shown in Figure 2. The impact of the attack is worldwide.
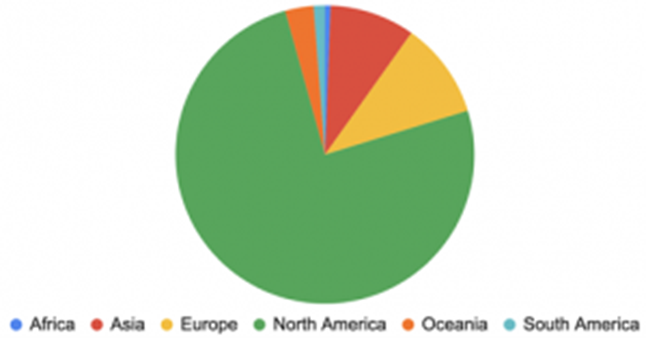
Figure 2:Victims Distribution by Continent
The top countries with most victims are:
| Country Name | Victim Count |
| United States | 110 |
| Canada | 13 |
| Israel | 5 |
| Denmark | 5 |
| Australia | 4 |
| United Kingdom | 4 |
4.0 Defense Against SUNBURST with Stellar Cyber’s Open XDR platform
While SUNBURST is a stealthy and sophisticated threat, it does leave important traces to identify itself.
First, it is important for enterprises to store artifacts and traces regarding their networks into a security data lake such as the Open XDR platform from Stellar Cyber. When the attack is known, around the world, enterprises can quickly check the indicators against the historic data to reveal whether they got breached. For sophisticated threats like SUNBURST, the C2 (Command & Control) Domains and IP addresses usually are strong signals. For SUNBURST in particular, the C2 domain has a pattern of avsvmcloud.com. The enterprises need to deploy a good NTA (NDR) solution that is capable of logging important metadata from the traffic of DNS and other important L7 application protocols. Data ingestion through DNS logs are also helpful, but it might not capture the signals if the attacker utilizes public DNS such as Google DNS (8.8.8.8) etc. Moreover, with advanced DGA detections and other network level anomaly detections from Stellar Cyber, the enterprises may find unknown suspicious signals earlier.
Second, the EDR endpoint telemetrics are also very important and useful, together with network level signals, with the Open XDR platform from Stellar Cyber, the enterprises may identify the suspicious lateral movement inside the company and detect the SUNBURST like malware through both Threat Intelligence or unknown suspicious activities. The Stellar Cyber platform can store and correlate signals from multiple data sources and have ML based detections to detect unknown suspicious activities.
5.0 Conclusions
In this blog, we shared some clues on how SolarWinds got hacked, and analyzed DGA domain data, showed the data study on affected domains, as well as provided some suggestions on defense.
The post SolarWinds SUNBURST Backdoor DGA and Infected Domain Analysis appeared first on Cybersecurity Insiders.
March 05, 2021 at 11:07PM






0 comments:
Post a Comment