Microsoft has built its Windows Defender Antivirus solution into the Windows 10 operating system, and that provides a good foundation for protecting your endpoints. But as the recent discovery of a new zero-day attack reminds us, it’s not good enough.
Several journalists including Tara Seals at Threatpost, Lucian Armasu with Tom’s Hardware and Dark Reading’s Kelly Sheridan reported on how a security researcher who goes by “SandboxEscaper” used Twitter to not only disclose a Windows vulnerability, but also express frustration over Microsoft’s vulnerability reporting process. The tweet has since been deleted, but the ESET researchers who identified the exploit posted a cleaned-up version of what they describe as “a rather acerbic tweet”:
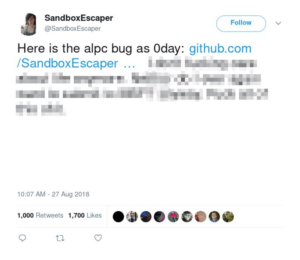
SandboxEscaper had discovered a bug in the Advanced Local Procedure Call (ALPC) interface of the Windows 7 and Windows 10 Task Schedulers that could allow an attacker to gain administrative rights, and placed the proof-of-concept (PoC) source code on GitHub!
And as Armasu writes, “not surprisingly, malicious actors swooped in days later to use the bug for their benefit.”
A group called PowerPool used the source code to create malware to gain write access to the GoogleUpdate.exe function – the legitimate updater for Google applications that runs with admin privileges – then attempted to use it to gain system privileges on their victims’ machines.
Granted, this is a bizarre story because of SandboxEscaper’s decision to include the full source code in his PoC, which made PowerPool’s work much easier. But it also illustrates two key points:
- Just how vulnerable endpoints running on Windows 10 are to unknown and zero-day attacks.
- Why Defense in Depth is the golden standard in security. This layered protection approach is important not only for cases where attackers bypass one or multiple security layers, but also for situations when one of the security products hasn’t been updated or is malfunctioning.
Windows Defender Antivirus is an example of a solution that follows the Negative Security model, focusing on identifying and blocking bad actors and malware. SE Labsearlier this year tested a variety of anti-malware solutions to determine their effectiveness at detecting and/or protecting against “well-established techniques and public email and web-based threats.” Windows Defender Antivirus only scored 76% in SE Labs’ Total Accuracy Rating.1
This points to the fact that following the Negative model by relying on products like Windows Defender Antivirus that focus only on blocking the “bad” does not enable you to create a true “defense in depth” approach. That requires combining Negative and Positive Security models.
Positive Security defines what is allowed (aka “good” or “known”), and rejects everything else. Having both Positive and Negative Security solutions in your security stack provides the highest possible endpoint protection. That is what Nyotron’s PARANOID solution delivers.
PARANOID is based on an OS-Centric Positive Security approach leveraging Behavior Pattern Mapping that maps all legitimate operating system behavior. The amount of good behavior is finite because there are just a handful of operating systems out there, and they change infrequently, especially in the way they operate with the file system and networking. That makes it possible to identify actions that can cause system damage or lead to data theft, including unknown, fileless and and zero-day malware. Nyotron has mapped all of the right ways to perform things on an endpoint and will block any activities outside of that finite list of legitimate OS behavior from executing.
PARANOID can even protect endpoints that have already been infected prior to product’s installation by analyzing and blocking every system call having a potential to cause damage to a system or data.
To learn more about how PARANOID can make your Windows 10 endpoints truly secure, download our datasheet “Nyotron and Windows 10 More Secure Together”. Note, this means leveraging both Windows Defender and Nyotron’s PARANOID working together and complementing each other, rather than advocating for a rip and replace approach.
For more information on how PARANOID enables you to create a multi-layered defense that strikes a balance between Negative and Positive Security, use this link to schedule a 15 minute chat with our team.
1SE Labs, “Enterprise Endpoint Protection Jan – Mar 2018”
The post Windows Defender Antivirus: Good Isn’t Good Enough appeared first on Cybersecurity Insiders.
September 18, 2018 at 06:10PM






0 comments:
Post a Comment