by Sergio Loureiro, Cloud Security Product Director at Outpost24
Containers have become very popular with DevOps as a way to increase speed and agility. However, with hackers utilizing vulnerabilities in Docker container images to compromise hosts and launch malicious containers – how to identify this at the time of development and prevent security costing you later?
What is container security?
Containers are shaping the future of software development creating an evolution in Cloud computing. Developers are embracing containerization in abundance and adopting it at an explosive rate due to its flexibility, portability and efficiency.
Like its name sake, the ‘container’ ship, you wouldn’t want to carry rogue containers with unknown goods so why do this in the virtual sense with your valuable applications and data assets? With containers comprising of many different components, organizations need to ensure no vulnerabilities exist and mitigate risks before your container and its contents (comprising of software libraries, and vulnerabilities if you are not careful) reaches the end customer.
Common vulnerabilities in Docker and Kubernetes
Whilst the adoption of containers has brought Development and IT operations closer together to facilitate the DevOps workflow, storing them securely in the registries and running them safely remains a challenge. It’s becoming clear that vulnerabilities could easily be hidden in containers, and a misconfigured port could leave you open to abuse for things like crypto-mining.
Hackers are finding new methods to gain access to the host using compromised containers. The infamous runc vulnerability is now patched but it is the kind of issue that keeps security teams up at night. The isolation between containers and the host operating system is an important barrier to avoid attacks from becoming widespread, however it’s easily overlooked in the speed of DevOps. Docker Hub is widely used throughout the industry as a repository for finding and sharing container images, despite its convenience, these should be handled with caution and you should have sufficient analysis before bringing them into your private registry to ensure no security flaws exist.
Kubernetes is complex and also has a large attack surface. What is still a prevalent threat is the possibility of privileged escalation, with multi-user systems designed to enable groups of developers working on independent applications at a time. Misconfiguration is a big issue here since Kubernetes allows pods to talk through the API, so if one service is compromised, it could affect an entire cluster or network. But often developers are not familiar with the concepts of network policies and fall short in ensuring least privilege policies and access controls are in place to reduce network risk.
How to secure containerized apps in agile DevOps
As the enterprise workload evolves, organizations are increasingly opting for containerized applications and serverless PaaS. Security leaders must look to address challenges related to the highly dynamic cloud environments, where conventional security perimeter protection tools have become redundant.
According to Gartner, “protection requirements for cloud native applications are evolving and span virtual machines, containers and serverless workloads in public and private clouds.” We have seen an evolution of workloads towards smaller and shorter spans as seen below.
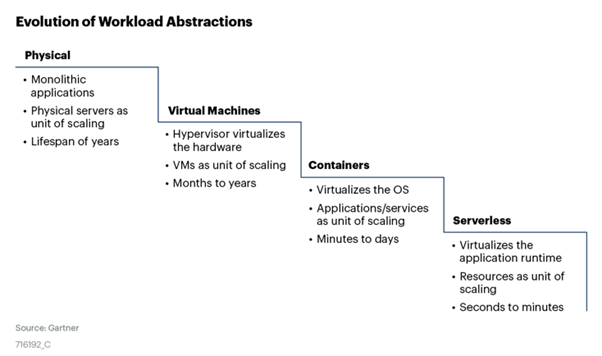
Therefore, security tools that will support workloads protection and configuration assessment in newer architectures using microservices and container-as-a-service have become all the more important to comprehensively secure the paradigm shift.
Inspect container images early in development
Developers no longer write all of their own code, instead, they assemble, configure and automate components from public registries to quickly add functionality. Container composition analysis should therefore be deployed earlier on in development for comprehensive image inspection, ensuring critical vulnerabilities in base images are identified and resolved before moving on to the next stage, and this process should be fully automated for easy adoption and fast remediation by developers.
Whether developed in-house or outsourced, container inspection is vital to help reduce the risk exposure of enterprises who source and use public images from third parties like Docker Hub. If a vulnerable container was brought into the enterprise’s private registry unknowingly, this could disrupt the integrity of the application and revenue generating operations down the line.
Prevent application layer attacks before deployment
Once you have developed and tested container images for vulnerabilities, it is time to prepare for build and deployment. From a security point of view, the next step is to test for application vulnerabilities. Security flaws such as injection, cross site scripting XSS and sensitive data exposure are common for web applications, so checking them against OWASP Top 10 is the most effective way to minimize risk, and this must be done during the QA or validation phase before deployment. Once again, this step should be completely automated during the build process and integrated in the CI/CD pipeline to ensure a smooth workflow between DevOps and SecOps.
Harden container host to avoid misconfigurations
Finally, once the application is ready for production enterprises must be sure that the security of the systems that your containers are running on is hardened according to best practices. Outpost24 supports CIS Docker and CIS Kubernetes benchmark assessment, the de facto and most comprehensive configuration and hardening guideline to ensure the correct security controls are in place for the host as well as the docker daemon.
Path to DevSecOps success
Securing your container with in-built software composition analysis will save you money and time fixing issues in the future. Why? Well, you wouldn’t go to all that time and effort to place your newly constructed application using faulty building blocks? And having used different containers without running necessary security checks could lead to a plethora of vulnerabilities. Both within the different container images and your own containers – leaving you open to risk and costing you more in the long run by finding vulnerabilities during production and impacting your entire SDLC.
Beyond the tools and technologies, the challenge of container security lies in DevOps and SecOps collaboration. As developers are given more accountability around security it is tricky in practice, as Developers are not security experts and have a different set of priorities of their own. So with DevOps leading the way in container adoption, SecOps need to reign this in and ensure security best practices are built into the SDLC workflow to support the use of containers at enterprise level. The only way to achieve true DevSecOps efficiency is shifting left – educating developers on secure coding practice, adding security automation and integrating container assessment seamlessly across the SDLC to ensure security is not a roadblock but an enabler for faster and safer releases.
Access your docker containers today!
The post Container Inspection for Cloud DevOps appeared first on Cybersecurity Insiders.
January 16, 2021 at 11:40PM






0 comments:
Post a Comment